Exploring the Exciting New Linux Distros of 2021
New Linux Distros in 2021: Exploring the Evolving Landscape of Open-Source Operating Systems
The year 2021 has brought forth a wave of exciting new Linux distributions, each offering unique features and improvements to cater to the diverse needs of users. As the open-source community continues to grow, these new distros showcase the ongoing innovation and dedication of developers worldwide. In this article, we will explore some of the noteworthy Linux distributions that have emerged in 20
1. Pop!_OS 21.04: Developed by System76, Pop!_OS is gaining popularity for its focus on productivity and user experience. The latest release introduces a refined design, improved performance, and enhanced gaming capabilities. With its intuitive interface and robust software support, Pop!_OS aims to provide a seamless experience for both casual users and professionals.
Fedora 34: Fedora is known for its cutting-edge technologies and commitment to open-source principles. The latest release brings significant improvements in performance, security features, and software management. With updated versions of GNOME desktop environment and Btrfs filesystem support, Fedora 34 offers a solid foundation for developers and enthusiasts alike.
elementary OS 6: Built with simplicity and elegance in mind, elementary OS has always been appreciated for its clean user interface reminiscent of macOS. The newest iteration introduces several visual enhancements along with improved system settings and refined application designs. With a focus on privacy and ease-of-use, elementary OS continues to captivate users seeking a polished desktop experience.
EndeavourOS: Aimed at providing a hassle-free Arch Linux experience, EndeavourOS offers an easy-to-install system with pre-configured desktop environments like Xfce, KDE Plasma, and more. This newcomer focuses on simplicity while maintaining compatibility with Arch’s vast software repositories. EndeavourOS appeals to users who desire the flexibility of Arch without the complexities of manual installation.
Garuda Linux: Garuda Linux aims to provide a performance-oriented and visually appealing Arch-based distribution. With its unique “Garuda Gamer” edition, this distro comes preloaded with gaming tools and optimizations, making it an attractive choice for gamers. Garuda Linux also offers various desktop environments, including KDE Plasma, Xfce, and GNOME.
Ubuntu 21.04: As one of the most well-known Linux distributions, Ubuntu continues to evolve with each release. The latest version brings updated packages, improved performance, and enhanced support for Raspberry Pi devices. Ubuntu 21.04 also introduces the Wayland display server as the default option for select hardware configurations, offering a smoother graphical experience.
Nitrux: Nitrux is a visually striking distribution that combines the power of Ubuntu with the versatility of KDE Plasma desktop environment. Known for its vibrant and modern design, Nitrux offers a user-friendly experience while incorporating cutting-edge technologies like AppImage support and ZFS filesystem integration.
These are just a few examples of the exciting new Linux distributions that have emerged in 20
Each distro brings its own set of features and strengths to cater to different user preferences and requirements. Whether you are a developer seeking bleeding-edge technologies or a casual user looking for an intuitive interface, there is undoubtedly a Linux distribution out there that suits your needs.
The open-source community’s dedication to innovation continues to drive the development of new distros, pushing boundaries and expanding possibilities in the world of operating systems. As we move forward in 2021 and beyond, it will be fascinating to witness how these new Linux distributions evolve further while inspiring future developments in the ever-growing open-source ecosystem.
8 Frequently Asked Questions about New Linux Distros in 2021: A Comprehensive Guide
- What are the best new Linux distros to try in 2021?
- How do I choose the right Linux distribution for my needs?
- Are there any new Linux distros specifically designed for gaming in 2021?
- Which new Linux distributions offer a user-friendly interface for beginners?
- Can I upgrade my current Linux distribution to one of the new releases in 2021?
- What are the system requirements for the latest Linux distros in 2021?
- Are there any notable security features or enhancements in the new Linux distros this year?
- How can I contribute to or get involved with the development of these new Linux distributions?
What are the best new Linux distros to try in 2021?
In 2021, several new Linux distributions have emerged, each offering unique features and experiences. While the “best” distro ultimately depends on individual preferences and requirements, here are some noteworthy options worth exploring:
- Pop!_OS 21.04: Developed by System76, Pop!_OS focuses on productivity and user experience. It offers a refined design, improved performance, and enhanced gaming capabilities.
- Fedora 34: Known for its cutting-edge technologies, Fedora brings improvements in performance, security features, and software management. It provides a solid foundation for developers and enthusiasts.
- elementary OS 6: With its clean and elegant interface reminiscent of macOS, elementary OS prioritizes simplicity and ease-of-use while emphasizing privacy. It offers refined application designs and improved system settings.
- EndeavourOS: Aimed at providing an easy Arch Linux experience, EndeavourOS offers a user-friendly installation process with pre-configured desktop environments like Xfce and KDE Plasma.
- Garuda Linux: This Arch-based distribution focuses on performance and aesthetics. Garuda Linux’s “Garuda Gamer” edition comes with gaming tools and optimizations, making it appealing to gamers.
- Ubuntu 21.04: As one of the most popular Linux distributions, Ubuntu continually evolves with each release. The latest version brings updated packages, improved performance, enhanced Raspberry Pi support, and the Wayland display server as the default option for select hardware configurations.
- Nitrux: Combining Ubuntu’s power with the versatility of KDE Plasma desktop environment, Nitrux stands out with its visually striking design. It incorporates modern technologies like AppImage support and ZFS filesystem integration.
These distros represent a diverse range of choices catering to different needs such as productivity, gaming, simplicity, or cutting-edge technologies. Exploring these options can help you find a Linux distribution that aligns with your specific preferences and requirements in 2021.
How do I choose the right Linux distribution for my needs?
Choosing the right Linux distribution can seem like a daunting task, given the wide range of options available. However, by considering a few key factors, you can find a distribution that aligns with your needs and preferences. Here are some steps to help you make an informed decision:
- Purpose: Determine the primary purpose of using Linux. Are you looking for a general-purpose desktop OS, a server OS, or a specific use case like gaming or multimedia production? Identifying your purpose will narrow down the choices.
- User Experience: Consider your level of expertise and preferred user interface. If you are new to Linux or prefer a user-friendly experience, distributions like Ubuntu or Linux Mint might be suitable. For more advanced users or those seeking customization options, Arch Linux or Fedora could be worth exploring.
- Hardware Compatibility: Check if the distribution supports your hardware components out-of-the-box. Some distributions may have better driver support for specific hardware configurations, such as laptops with hybrid graphics cards or Wi-Fi adapters.
- Software Availability: Evaluate the availability of software packages and repositories for your desired distribution. Most mainstream distributions have vast software repositories, ensuring easy access to popular applications. However, if you require specific software not available in standard repositories, consider distributions like Arch Linux with its extensive AUR (Arch User Repository) support.
- Community Support: Assess the availability of community support and documentation for troubleshooting issues and learning resources. Active communities and forums can be valuable when seeking assistance or sharing knowledge with other users.
- Security and Stability: Consider your requirements regarding security and stability. Some distributions prioritize cutting-edge features but may have occasional stability issues due to frequent updates (e.g., Arch Linux). Others focus on long-term stability (e.g., Debian), which may sacrifice access to the latest software versions.
- Specialized Needs: If you have specialized needs such as ethical hacking (Kali Linux), privacy-focused browsing (Tails), or lightweight systems (Puppy Linux), explore distributions tailored to those specific use cases.
- Try Live Versions: Many Linux distributions offer “live” versions that allow you to boot from a USB or DVD without installing. Trying out different distributions in this manner can give you a hands-on experience and help you assess their suitability before committing.
Ultimately, the right Linux distribution depends on your personal preferences, technical requirements, and intended use. It’s worth experimenting with different distributions until you find one that feels comfortable and meets your needs effectively. Remember, Linux offers flexibility, so don’t hesitate to switch distributions if your requirements change over time.
Are there any new Linux distros specifically designed for gaming in 2021?
Yes, there are several Linux distributions that have emerged in 2021 with a specific focus on gaming. These distros aim to provide an optimized gaming experience by incorporating gaming-related tools, drivers, and pre-installed software. Here are a few notable examples:
- Garuda Linux: Garuda Linux offers a dedicated edition called “Garuda Gamer.” It comes with various gaming tools and optimizations out of the box, including the Steam gaming platform, Lutris game manager, and custom kernel settings for improved performance.
- Pop!_OS 21.04: While not exclusively focused on gaming, Pop!_OS has gained popularity among gamers due to its emphasis on performance and compatibility with NVIDIA graphics cards. The latest release introduces enhanced gaming features and improved driver support.
- Manjaro Gaming Edition: Manjaro is a user-friendly Arch-based distribution that offers a dedicated Gaming Edition. It includes popular gaming software like Steam, Wine, and PlayOnLinux pre-installed for easy setup and access to a wide range of games.
- GamerOS: Built specifically for gaming, GamerOS is designed as a console-like operating system based on Arch Linux. It provides an optimized environment for running games through the Steam Big Picture mode interface.
These distros prioritize providing an out-of-the-box gaming experience by incorporating the necessary software and optimizations to maximize performance and compatibility with popular games. They aim to make it easier for gamers to transition to Linux while enjoying their favorite titles without hassle.
It’s worth noting that while these distros offer specific gaming-focused features, many other mainstream distributions can also be customized for optimal gaming performance by installing relevant software and drivers manually.
Which new Linux distributions offer a user-friendly interface for beginners?
Several new Linux distributions offer a user-friendly interface specifically designed for beginners. Here are a few notable examples:
- Pop!_OS: Developed by System76, Pop!_OS focuses on providing a streamlined and intuitive experience for users. Its clean and modern interface, along with its user-friendly installer, makes it an excellent choice for beginners.
- elementary OS: Known for its sleek and macOS-like design, elementary OS offers a visually appealing and easy-to-use interface. It emphasizes simplicity and comes with pre-installed applications that cater to everyday tasks.
- Zorin OS: Designed to resemble the familiar layout of Windows, Zorin OS aims to make the transition from Windows to Linux seamless for beginners. It offers a polished desktop environment with an intuitive start menu and customizable appearance.
- Linux Mint: Renowned for its user-friendly approach, Linux Mint provides a traditional desktop environment with a classic layout similar to Windows 7. It includes various useful tools and codecs out of the box, making it convenient for newcomers.
- Ubuntu: As one of the most popular Linux distributions, Ubuntu has made significant efforts towards improving its user experience over the years. With its Unity or GNOME desktop environments, Ubuntu offers simplicity and ease of use for beginners.
These distributions prioritize accessibility and ease-of-use without compromising on functionality or performance, making them ideal choices for those new to Linux. They provide a welcoming environment for beginners to explore the world of open-source software without feeling overwhelmed by complex configurations or unfamiliar interfaces.
Can I upgrade my current Linux distribution to one of the new releases in 2021?
Yes, it is usually possible to upgrade your current Linux distribution to one of the new releases in 2021, depending on the specific distribution you are using. However, the upgrade process may vary slightly between different distributions.
Most Linux distributions provide official documentation and guides on how to upgrade from one version to another. It is recommended to consult the official documentation of your specific distribution for detailed instructions on how to perform the upgrade.
In general, the upgrade process involves updating your package repositories, upgrading installed packages, and applying any necessary configuration changes. Some distributions may provide a dedicated upgrade tool or command-line utility that automates this process.
Before proceeding with an upgrade, it is essential to back up your important data and configurations. While upgrades are designed to preserve user data, unexpected issues can occur during the process. Having a backup ensures that you can revert back if needed.
It’s worth noting that not all Linux distributions support direct upgrades from older versions to the latest releases. In some cases, you may need to perform a fresh installation of the new release instead of upgrading directly. Again, referring to the official documentation of your distribution will provide clarity on this matter.
Remember that each Linux distribution has its own release cycle and support policies. It’s advisable to stay informed about these policies and consider factors such as stability, compatibility with hardware and software, and availability of updates before deciding whether or not to upgrade.
Overall, upgrading your Linux distribution can be an exciting way to experience new features and improvements offered by the latest releases in 2021. Just make sure to follow proper procedures and guidelines provided by your distribution’s official documentation for a smooth transition.
What are the system requirements for the latest Linux distros in 2021?
The system requirements for the latest Linux distributions in 2021 can vary depending on the specific distro and its intended use. However, here are some general guidelines:
Pop!_OS 21.04:
– Minimum: 2 GHz dual-core processor, 4 GB RAM, 40 GB storage, Intel/AMD/NVIDIA graphics
– Recommended: Quad-core processor, 8 GB RAM or more, 120 GB storage or more, dedicated graphics card
Fedora 34:
– Minimum: 1 GHz processor, 2 GB RAM, 20 GB storage
– Recommended: Dual-core processor, 4 GB RAM or more, 40 GB storage or more
elementary OS 6:
– Minimum: Dual-core processor, 4 GB RAM, 15 GB storage
– Recommended: Quad-core processor, 8 GB RAM or more, SSD storage
EndeavourOS:
– Minimum: Dual-core processor, 2 GB RAM, 30 GB storage
– Recommended: Quad-core processor, 4 GB RAM or more, SSD storage
Garuda Linux:
– Minimum: Dual-core processor, 2 GB RAM, at least a few gigabytes of free disk space
– Recommended: Quad-core processor or higher, at least 4 GB RAM or more
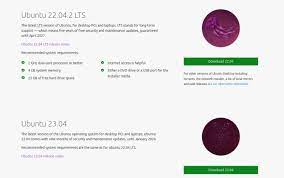
Ubuntu 21.04:
– Minimum: Dual-core processor (64-bit), at least a few gigabytes of RAM and disk space
– Recommended: Quad-core processor or higher (64-bit), at least 4 GB of RAM and several gigabytes of free disk space
Nitrux:
– Minimum: Dual-core processor (64-bit), at least a few gigabytes of RAM and disk space
– Recommended: Quad-core processor or higher (64-bit), at least 4 GB of RAM and several gigabytes of free disk space
It’s important to note that these are general recommendations, and the specific requirements may vary depending on factors such as the desktop environment, software packages installed, and intended usage (e.g., gaming or multimedia production). It’s always a good idea to check the official documentation or website of each Linux distribution for more detailed system requirements before installation.
Are there any notable security features or enhancements in the new Linux distros this year?
Absolutely! Security is a crucial aspect of any operating system, and Linux distributions are no exception. Many of the new Linux distros released in 2021 have introduced notable security features and enhancements to ensure user safety. Here are a few examples:
- Fedora 34: Fedora has always prioritized security, and the latest release is no different. Fedora 34 includes improvements such as stronger compiler flags, stack clash protection, and additional hardening options for packages. These measures help protect against various types of vulnerabilities and make it harder for attackers to exploit system weaknesses.
- Pop!_OS 21.04: Pop!_OS has introduced several security enhancements in its latest release. This includes improved disk encryption options during installation, making it easier for users to encrypt their data and protect their sensitive information. Additionally, Pop!_OS emphasizes secure boot configurations by integrating with the firmware’s Secure Boot feature.
- Ubuntu 21.04: Ubuntu continues its commitment to security with each release. In Ubuntu 21.04, there are various security-focused updates, including improved AppArmor profiles for applications, which restrict their access to system resources and enhance overall system security. The inclusion of Wayland as the default display server also provides better isolation between applications.
- Garuda Linux: Garuda Linux incorporates several security features to safeguard user systems. It utilizes firejail sandboxing technology by default for certain applications, which isolates them from the rest of the system and reduces potential attack vectors.
- Nitrux: Nitrux emphasizes security by integrating AppImage signatures into its software management process. This ensures that only verified and trusted applications can be installed on the system, minimizing the risk of installing malicious software.
These are just a few examples of how new Linux distros have focused on enhancing security in their releases this year. It’s important to note that maintaining up-to-date software repositories and promptly addressing vulnerabilities are common practices across most Linux distributions, further bolstering the overall security of the operating system.
How can I contribute to or get involved with the development of these new Linux distributions?
Contributing to the development of Linux distributions is a fantastic way to get involved in the open-source community and make a meaningful impact. Here are some ways you can contribute:
- Testing and Bug Reporting: One of the most valuable contributions you can make is testing new releases or development versions of Linux distributions. By reporting any bugs or issues you encounter, you help developers identify and fix problems, ensuring a more stable and reliable system for all users.
- Documentation and Translation: Linux distributions rely on comprehensive documentation to assist users in understanding and utilizing the software effectively. Contributing to documentation efforts by writing guides, updating existing content, or translating documentation into different languages helps make these distributions more accessible to users worldwide.
- Packaging and Software Maintenance: Linux distributions rely on repositories filled with packages that users can easily install and update. Contributing to packaging efforts involves maintaining software packages, ensuring they are up-to-date, well-maintained, and compatible with the distribution’s guidelines.
- User Support: Joining community forums, mailing lists, or chat channels dedicated to specific Linux distributions allows you to provide support and assistance to fellow users who may have questions or encounter issues. Sharing your knowledge and helping others is a valuable way to contribute.
- Development and Programming: If you have programming skills or want to learn, contributing code to open-source projects associated with Linux distributions can have a significant impact. This could involve fixing bugs, adding new features, improving performance, or optimizing existing code.
- Design and User Interface: If you have design skills or an eye for user experience (UX), contributing in this area can greatly enhance the visual appeal and usability of Linux distributions. This may involve creating icons, themes, wallpapers, or suggesting improvements for user interfaces.
- Financial Support: Many Linux distributions rely on donations from individuals or organizations to sustain their development efforts. Consider contributing financially if you are in a position to do so.
To get started with contributing, visit the official websites or community forums of the Linux distributions you are interested in. Look for information on their contribution guidelines, development processes, and ways to get involved. Remember that each distribution may have its own specific requirements and areas where they need assistance.
By actively participating in the development of Linux distributions, you become an integral part of the open-source community, shaping the future of these operating systems and empowering users worldwide.