The Power and Versatility of the Linux System
In a world dominated by operating systems like Windows and macOS, Linux stands out as a powerful alternative that offers unparalleled flexibility, security, and customization. Developed by Linus Torvalds in the early 1990s, Linux has grown into a robust and versatile operating system that powers everything from servers and supercomputers to smartphones and embedded devices. Let’s delve into what makes the Linux system so unique and why it has gained such a devoted following.
One of the key strengths of Linux lies in its open-source nature. Unlike proprietary operating systems, Linux is built on collaborative efforts from a global community of developers who contribute their expertise to create an ever-evolving platform. This open development model ensures continuous innovation, rapid bug fixes, and enhanced security measures. With thousands of eyes scrutinizing the code, vulnerabilities are quickly identified and addressed.
Linux’s versatility is another standout feature. It supports a wide range of hardware architectures, making it compatible with various devices, from low-power IoT devices to high-performance servers. This adaptability allows Linux to be deployed in diverse environments such as data centers, cloud computing platforms, embedded systems, and even on personal computers.
Moreover, Linux provides users with an extensive selection of distributions (commonly known as “distros”) tailored to different needs and preferences. Popular distros like Ubuntu, Fedora, Debian, and CentOS offer user-friendly interfaces coupled with comprehensive software repositories that make installing applications a breeze. These distros cater to different user levels – from beginners seeking simplicity to advanced users desiring complete control over their system.
One of the most significant advantages of using Linux is its exceptional stability. The modular design of the kernel ensures that individual components can be updated or replaced without affecting the entire system’s functionality. This approach minimizes downtime during updates or upgrades while maintaining system integrity.
Security is also at the core of the Linux philosophy. As an open-source system, Linux benefits from a large and vigilant community that constantly monitors and improves its security features. Vulnerabilities are swiftly identified, and patches are promptly released, making Linux inherently more secure than many closed-source alternatives. Additionally, Linux provides robust access controls and permissions, reducing the risk of unauthorized access to sensitive data.
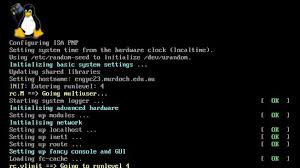
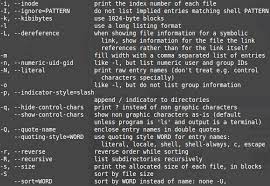
Linux’s command-line interface (CLI) is often regarded as a distinguishing feature. While it may seem daunting to newcomers, the CLI offers unparalleled power and efficiency for experienced users. It allows for precise control over system configurations, advanced scripting capabilities, and automation of repetitive tasks. However, it’s important to note that modern Linux distros also provide intuitive graphical user interfaces (GUIs) that rival the ease of use found in other operating systems.
The Linux system has come a long way since its humble beginnings. Today, it powers critical infrastructure worldwide and serves as a backbone for countless technological advancements. Its open-source nature fosters collaboration and empowers users to shape their computing experience according to their needs.
Whether you’re an enthusiast seeking customization options or an enterprise looking for a reliable and secure platform, Linux offers a compelling solution. Its versatility, stability, security features, and vibrant community make it an exceptional choice for those who value freedom of choice and innovation.
Embrace the power of Linux – join millions of users worldwide who have embraced this remarkable operating system and experience the endless possibilities it provides.
7 Advantages of Linux: Security, Cost, Reliability, Performance, Customisation, Compatibility, and Ease of Use
- Security – Linux is one of the most secure operating systems available, with built-in security features and regular updates to keep your system safe from malicious attacks.
- Cost – Linux is free and open source, meaning you don’t have to pay for a license or upgrade fees.
- Reliability – The Linux kernel is very reliable and stable, making it an ideal choice for mission critical applications that require high uptime levels.
- Performance – Linux can be customised to run efficiently on almost any hardware configuration, providing excellent performance even on low-end machines.
- Customisation – With its open source codebase, users are able to modify and customise their system however they like in order to suit their specific needs or preferences.
- Compatibility – Linux has a wide range of compatible software packages available, many of which are free or cost much less than their Windows counterparts do.
- Ease of use – Despite the fact that many people think it’s difficult to use, modern versions of Linux come with user-friendly graphical interfaces that make it easy for anyone to get started quickly
5 Cons of Linux System: Limited Software Availability, Lack of Support, Complexity, Security Risks, and Hardware Compatibility Issues
- Limited software availability – Linux systems are not compatible with many of the popular programs and applications that users may need to use.
- Lack of support – As Linux is open-source, there is no official provider of technical or customer support for the system.
- Complexity – The user interface can be complex and difficult for novice users to understand and navigate, requiring some basic knowledge of computers before use.
- Security risks – Although Linux systems have a good reputation for security, they are still vulnerable to viruses and malware if not kept up-to-date with patches and security updates.
- Hardware compatibility issues – Not all hardware components are compatible with Linux systems, so it’s important to check this before installation or purchase new components specifically designed for the system.
Security – Linux is one of the most secure operating systems available, with built-in security features and regular updates to keep your system safe from malicious attacks.
Enhancing Security: The Strength of Linux
When it comes to operating systems, security is a paramount concern. In this digital age, where threats to our data and privacy are ever-present, having a secure system is crucial. Linux, renowned for its robustness and reliability, stands out as one of the most secure operating systems available today.
Linux’s exceptional security can be attributed to several key factors. Firstly, its open-source nature allows for continuous scrutiny by a vast community of developers worldwide. This collaborative effort ensures that vulnerabilities are quickly identified and addressed, making Linux inherently more secure than closed-source alternatives.
Additionally, Linux comes equipped with built-in security features that fortify the system from potential threats. From access controls to file permissions and encryption mechanisms, Linux provides a comprehensive suite of tools to protect your data and ensure only authorized users can access sensitive information.
Furthermore, regular updates play a vital role in maintaining the security of any operating system. Linux excels in this aspect as well. With an active development community constantly working on improvements and bug fixes, updates are regularly released to address emerging security concerns promptly. These updates not only enhance the system’s stability but also ensure that your Linux environment remains resilient against malicious attacks.
Linux’s security extends beyond just the operating system itself; it also benefits from the robustness of its software repositories. These repositories provide a vast collection of applications that have undergone rigorous testing and scrutiny before being made available for installation. This meticulous review process minimizes the risk of installing compromised or malicious software on your system.
Moreover, Linux’s emphasis on user control adds another layer of security. With Linux, you have complete control over your system’s configurations and permissions. This level of granularity empowers users to fine-tune their security settings according to their specific requirements.
While no system is entirely immune to attacks or vulnerabilities, Linux’s strong foundation in security measures makes it highly resilient against malicious threats. Its proactive approach towards security, coupled with regular updates and a vigilant community, ensures that your Linux system remains well-guarded.
Whether you are a home user concerned about personal privacy or an organization safeguarding critical data, Linux offers peace of mind. By choosing Linux, you are opting for an operating system that prioritizes security and actively works towards keeping your system safe from malicious attacks.
Embrace the security prowess of Linux and experience the confidence that comes with knowing your digital world is protected. With Linux, you can navigate the online landscape with peace of mind, focusing on what matters most to you while leaving the worries of cyber threats behind.
Cost – Linux is free and open source, meaning you don’t have to pay for a license or upgrade fees.
The Cost Advantage of the Linux System
In a world where software licenses and upgrade fees can quickly add up, Linux stands out as a cost-effective solution that offers incredible value. One of the most significant advantages of the Linux system is its price tag – it’s free and open-source. Unlike proprietary operating systems, Linux allows users to access, use, and modify the source code without any licensing restrictions.
The freedom to use Linux without paying for a license brings numerous benefits. Firstly, it eliminates the financial burden associated with purchasing an operating system. Whether you’re an individual user or a business owner, this cost-saving aspect can make a significant difference in your budget allocation. Instead of investing in expensive licenses for other operating systems, you can allocate those funds towards other essential areas or invest in hardware upgrades.
Furthermore, since Linux is open-source, it encourages collaboration and community-driven development. A global community of passionate developers constantly contributes to improving the system’s functionality and security. This collaborative effort ensures that Linux remains at the forefront of innovation without relying on costly research and development budgets.
Another advantage of Linux’s cost-effectiveness is its ability to run efficiently on older hardware. While other operating systems may require frequent hardware upgrades to keep up with their resource demands, Linux can breathe new life into older machines. This means you can extend the lifespan of your existing hardware infrastructure without compromising performance or productivity.
Additionally, as there are no upgrade fees associated with Linux, users have complete control over when and how they choose to update their systems. This flexibility allows businesses to plan their upgrades strategically based on their specific needs and budgetary considerations.
The cost advantage of Linux extends beyond individual users or small businesses; it also benefits large enterprises and organizations. With no licensing costs or restrictions on scalability, businesses can deploy Linux across multiple machines without incurring additional expenses. This scalability makes it an ideal choice for data centers and cloud computing environments where cost optimization is crucial.
It’s important to note that although Linux is free, it doesn’t mean it lacks in quality or features. In fact, many Linux distributions offer a plethora of powerful tools and applications that rival their proprietary counterparts. From office productivity suites to multimedia editing software and development environments, Linux provides a comprehensive ecosystem that caters to various user needs.
In conclusion, the cost advantage of the Linux system is undeniable. By eliminating licensing fees and upgrade costs, Linux empowers users with a cost-effective solution that doesn’t compromise on performance or functionality. Whether you’re an individual seeking an affordable operating system or a business aiming to optimize your IT budget, Linux offers a compelling choice that delivers exceptional value. Embrace the freedom and cost-effectiveness of Linux today and unlock the full potential of your computing experience.
Reliability – The Linux kernel is very reliable and stable, making it an ideal choice for mission critical applications that require high uptime levels.
The Unmatched Reliability of Linux: Ensuring High Uptime for Mission-Critical Applications
When it comes to reliability and stability, the Linux system stands head and shoulders above its competitors. The Linux kernel, the core component of the operating system, has garnered a well-deserved reputation for its rock-solid performance, making it the preferred choice for mission-critical applications that demand high uptime levels.
One of the key reasons behind Linux’s reliability lies in its design philosophy. The Linux kernel is built with a focus on stability and robustness, ensuring that it can handle heavy workloads and operate flawlessly even under challenging conditions. Its modular architecture allows for independent updates and replacements of components without affecting the overall system’s stability. This means that critical applications can continue running smoothly while individual parts are being updated or fixed.
The open-source nature of Linux also contributes to its reliability. With a vast community of developers constantly scrutinizing the code, vulnerabilities are quickly identified and resolved. This collaborative effort ensures that potential issues are addressed promptly, minimizing any potential downtime or disruptions. Furthermore, the transparency of open-source development allows users to have greater control over their systems, enabling them to fine-tune configurations to optimize performance and reliability.
Linux’s reliability is particularly crucial for mission-critical applications that require uninterrupted operation. Industries such as finance, healthcare, telecommunications, and aerospace rely on these applications to perform vital functions 24/7 with minimal margin for error. Whether it’s processing financial transactions or managing critical healthcare systems, any downtime can result in significant financial losses or compromise public safety.
The stability and resilience of Linux make it an ideal choice for these demanding scenarios. Its ability to handle heavy workloads without faltering ensures continuous operation even under immense pressure. Additionally, Linux offers various features that enhance reliability further, such as fault-tolerant file systems and advanced monitoring tools that provide real-time insights into system health.
Moreover, Linux excels at server management, which is crucial for maintaining high uptime levels. Its efficient resource allocation and process management capabilities allow administrators to optimize system performance and ensure that critical applications receive the necessary resources to operate smoothly. Furthermore, Linux’s ability to handle multiple concurrent tasks while maintaining stability makes it an excellent choice for servers that need to handle heavy workloads.
The reliability of the Linux system has made it a trusted platform for critical infrastructure worldwide. From web servers and database systems to telecommunications networks and supercomputers, Linux powers a vast array of mission-critical applications across various industries.
In an increasingly interconnected world where downtime can have far-reaching consequences, choosing a reliable and stable operating system is paramount. Linux’s proven track record in delivering high uptime levels, combined with its robustness and community-driven development model, positions it as the go-to choice for organizations seeking unwavering reliability for their mission-critical applications.
Embrace the unparalleled reliability of Linux and experience peace of mind knowing that your critical systems will operate flawlessly even under the most demanding circumstances. With Linux, you can trust in its stability, ensuring uninterrupted operation and safeguarding your business from costly disruptions.
Unlocking the Performance Potential of Linux
When it comes to performance, the Linux system shines brightly, offering a level of customizability that sets it apart from other operating systems. Linux has the remarkable ability to adapt and run efficiently on a wide range of hardware configurations, delivering exceptional performance even on low-end machines. Let’s explore how Linux achieves this and why it is a top choice for those seeking optimal performance.
One of the key advantages of Linux is its flexibility. Unlike other operating systems that may be resource-heavy or require specific hardware specifications, Linux can be tailored to suit almost any hardware configuration. This means that even older or low-end machines can benefit from the power and efficiency that Linux brings to the table.
Linux allows users to customize various aspects of their system, such as the choice of desktop environment, kernel configuration, and software packages. This level of customization empowers users to fine-tune their system settings according to their specific needs and hardware capabilities. By eliminating unnecessary background processes and optimizing resource allocation, Linux can maximize performance on any given machine.
Furthermore, Linux distributions offer lightweight versions specifically designed for low-end hardware. These lightweight distributions strip away resource-intensive components while retaining essential functionality, resulting in a leaner and more responsive system. This enables users with older or less powerful machines to enjoy a smooth computing experience without compromising on performance.
In addition to customization options, Linux benefits from its efficient design and streamlined architecture. The modular nature of the Linux kernel allows for efficient memory management and optimized task scheduling. This means that system resources are utilized effectively, resulting in faster response times and improved overall performance.
Moreover, Linux’s open-source nature fosters continuous development and optimization by a vast community of contributors worldwide. These dedicated individuals work tirelessly to enhance various aspects of the operating system, including performance improvements. As a result, updates and optimizations are regularly released, ensuring that Linux remains at the forefront of efficiency.
The excellent performance offered by Linux is not limited to desktop or laptop computers. Linux is widely used in server environments, where its efficiency and stability are highly sought after. Whether it’s running a web server, a database server, or a cloud computing platform, Linux consistently delivers exceptional performance, making it the preferred choice for many businesses and organizations.
In conclusion, Linux’s ability to be customized and optimized for different hardware configurations is what sets it apart in terms of performance. From low-end machines to high-end servers, Linux excels in delivering efficient and responsive computing experiences. With its flexible nature, streamlined architecture, and continuous development efforts from the open-source community, Linux proves time and again that it can unlock the true potential of any hardware setup.
So if you’re looking for an operating system that can breathe new life into your aging machine or maximize the capabilities of your powerful hardware, look no further than Linux. Experience the remarkable performance that Linux offers and witness firsthand how this open-source powerhouse can transform your computing experience.
Customisation – With its open source codebase, users are able to modify and customise their system however they like in order to suit their specific needs or preferences.
The Freedom of Customisation: Unleash Your Creativity with Linux
One of the most enticing advantages of the Linux system is its unparalleled customisation capabilities. With its open-source codebase, Linux empowers users to modify and tailor their operating system to perfectly suit their specific needs or preferences. This flexibility sets Linux apart from other closed-source alternatives, allowing users to unleash their creativity and truly make their system their own.
Unlike proprietary operating systems that restrict users to predefined settings and configurations, Linux offers an open canvas for customization. The open-source nature of the system means that anyone can access and modify the underlying source code. This not only encourages innovation but also gives users the freedom to adapt their system in ways that are simply not possible with closed-source systems.
Linux users have the ability to tweak every aspect of their operating environment, from the desktop environment and window managers to the kernel itself. Want a sleek and minimalist desktop? Choose from a wide range of lightweight desktop environments like Xfce or LXQt. Prefer a more feature-rich experience? Opt for popular environments like GNOME or KDE Plasma. The choice is yours.
Moreover, Linux provides an extensive selection of software packages that cater to different user preferences. Whether you’re a developer looking for powerful programming tools or a creative professional seeking specialized multimedia applications, Linux has got you covered. With its vast repositories of software, you can easily install and customize your system with the applications that best suit your needs.
Customisation extends beyond just software choices; it also encompasses system configurations. With Linux, you have full control over how your system behaves. Adjust power management settings to optimize battery life on a laptop or fine-tune network settings for optimal performance in your specific environment. Modify security settings according to your requirements or set up personalized shortcuts and automation scripts to streamline your workflow.
Linux’s customisation capabilities are not limited to individual users either. System administrators can create tailored distributions known as “spin-offs” or “remixes” to meet the specific needs of their organization. This allows for the creation of highly specialized systems optimized for particular tasks, such as multimedia production, scientific research, or server deployments.
The open-source nature of Linux also fosters a vibrant community of developers and enthusiasts who actively share their customizations and modifications. Online forums, blogs, and social media platforms are filled with tutorials, tips, and tricks to help users personalize their Linux experience. The collective knowledge and support from this community ensure that even beginners can dive into the world of customisation with ease.
In a world where personalization is increasingly valued, Linux stands as a beacon of freedom. Whether you’re an individual seeking a unique computing experience or an organization aiming to optimize productivity, Linux’s customisation capabilities empower you to create a system that perfectly aligns with your needs.
So why settle for a one-size-fits-all approach when you can have complete control over your operating system? Embrace the freedom of customisation that Linux offers and unlock your full creative potential. With Linux, your imagination is the only limit.
Compatibility – Linux has a wide range of compatible software packages available, many of which are free or cost much less than their Windows counterparts do.
Compatibility – A Boon for Linux Users
One of the standout advantages of using the Linux operating system is its remarkable compatibility with a wide range of software packages. This compatibility not only provides users with a vast selection of options but also offers significant cost savings compared to their Windows counterparts.
Linux boasts an extensive ecosystem of compatible software packages, catering to various needs and preferences. Whether you’re a student, professional, or hobbyist, you’ll find an abundance of applications that meet your requirements. From office productivity suites and graphic design tools to programming environments and multimedia software, Linux has it all.
What’s even more impressive is that many of these software packages are available for free or at significantly lower costs than their Windows equivalents. The open-source nature of Linux has fostered a vibrant community of developers who contribute their time and expertise to create high-quality software without the burden of licensing fees. This not only reduces the financial strain on users but also encourages collaboration and innovation within the Linux community.
For instance, when it comes to office productivity, Linux offers feature-rich alternatives such as LibreOffice and Apache OpenOffice. These suites provide word processing, spreadsheet management, presentation creation, and other essential tools comparable to Microsoft Office but without the hefty price tag. Similarly, graphic designers can take advantage of powerful open-source software like GIMP (GNU Image Manipulation Program) for image editing or Inkscape for vector graphics.
The compatibility doesn’t end there – developers can leverage robust programming environments like GCC (GNU Compiler Collection) and Python on Linux systems. These tools enable them to write code efficiently while benefiting from the vast array of libraries and frameworks available within the Linux ecosystem.
Moreover, multimedia enthusiasts will find an assortment of media players like VLC Media Player or Clementine Music Player that provide seamless playback for audio and video files across various formats. Additionally, content creators can rely on professional-grade video editing solutions like Kdenlive or Shotcut to produce stunning visuals without breaking the bank.
The compatibility of Linux with a wide range of software packages not only offers users a plethora of options but also empowers them to choose the tools that best suit their needs and preferences. The availability of free or cost-effective software ensures that individuals, small businesses, and educational institutions can access powerful applications without straining their budgets.
In conclusion, the compatibility of Linux with an extensive selection of software packages is a significant advantage for users. Not only does it provide a wealth of options for various tasks and industries, but it also offers substantial cost savings compared to proprietary alternatives. With Linux, you can enjoy the freedom to explore and utilize feature-rich applications without worrying about exorbitant licensing fees. Embrace the compatibility of Linux and unlock a world of possibilities while keeping your expenses in check.
Ease of use – Despite the fact that many people think it’s difficult to use, modern versions of Linux come with user-friendly graphical interfaces that make it easy for anyone to get started quickly
Demystifying Linux: The Ease of Use
Linux, often perceived as a complex and technical operating system, has made remarkable strides in recent years to dispel this notion. Contrary to popular belief, modern versions of Linux have embraced user-friendly graphical interfaces that make it accessible and straightforward for anyone to get started quickly. Let’s explore how Linux has evolved to become more user-friendly while retaining its powerful capabilities.
Gone are the days when Linux was solely associated with command-line interfaces and required extensive technical knowledge. Today, many Linux distributions offer intuitive graphical interfaces that rival the ease of use found in other popular operating systems. Distros like Ubuntu, Fedora, and Linux Mint provide visually appealing desktop environments that are familiar and welcoming to new users.
The beauty of these modern graphical interfaces lies in their simplicity. They feature well-designed menus, taskbars, and icons that allow users to navigate effortlessly through applications and settings. With a few clicks or taps, users can launch programs, browse the web, manage files, and perform various tasks without any prior knowledge of command-line operations.
Moreover, software installation on Linux has become remarkably user-friendly. Package managers such as Ubuntu Software Center or GNOME Software provide easy-to-use interfaces where users can search for applications by name or category. Installing software is as simple as selecting the desired application and clicking the install button – no need to worry about manually downloading files or dealing with complex installation processes.
Another advantage of modern Linux distributions is the availability of comprehensive documentation and online support communities. If users encounter any difficulties or have questions about using their Linux system, they can find answers through official documentation or engage with helpful communities online. These resources empower users to troubleshoot issues effectively and learn more about utilizing their Linux system efficiently.
Furthermore, many popular applications are now readily available on Linux platforms. Office suites like LibreOffice offer robust alternatives to proprietary software packages. Web browsers such as Firefox and Chrome have native versions for Linux, ensuring a seamless browsing experience. Multimedia software like VLC Media Player and GIMP for image editing are also widely accessible. This growing availability of applications ensures that users can accomplish their tasks without compromising compatibility or functionality.
The ease of use in modern Linux distributions is not only beneficial for beginners but also for experienced users who appreciate a streamlined and efficient workflow. The graphical interfaces provide a visually pleasing and intuitive environment, allowing users to focus on their work rather than spending time on technical configurations.
Linux’s commitment to ease of use is a testament to its adaptability and inclusivity. By embracing user-friendly interfaces, Linux has opened its doors to a wider audience, making it an attractive choice for both individuals and organizations seeking an alternative operating system.
So, if you’ve been hesitant to explore Linux due to its perceived complexity, it’s time to reconsider. With its user-friendly graphical interfaces, extensive software availability, and supportive communities, Linux offers an accessible and powerful computing experience for everyone. Embrace the ease of use that Linux provides and unlock the vast potential this remarkable operating system has to offer.
Limited software availability – Linux systems are not compatible with many of the popular programs and applications that users may need to use.
Addressing the Limited Software Availability Conundrum in Linux Systems
Linux systems have long been praised for their stability, security, and customizability. However, one common criticism is the perceived limited availability of software compared to other operating systems like Windows or macOS. It is true that Linux may not always have direct compatibility with certain popular programs and applications that users may rely on. However, it’s essential to understand the nuances of this con and explore the solutions that exist within the Linux ecosystem.
The primary reason for the perceived limited software availability in Linux is rooted in its open-source nature. Unlike proprietary operating systems, where developers often prioritize creating software exclusively for a specific platform, Linux provides a more diverse landscape. This diversity leads to a wider range of software options but can also result in some programs being initially unavailable or requiring additional steps for installation.
Fortunately, the Linux community has developed several approaches to mitigate this issue. Firstly, many popular software developers now recognize the growing demand for Linux-compatible versions of their applications. As a result, they are increasingly offering official support or developing alternative versions specifically tailored for Linux environments.
Additionally, there are numerous open-source alternatives available on Linux that can serve as substitutes for popular proprietary software. For instance, LibreOffice provides a comprehensive office suite compatible with Microsoft Office files. GIMP offers powerful image editing capabilities akin to Adobe Photoshop. These alternatives may require some adjustment and learning but can often fulfill users’ needs without compromising functionality.
Furthermore, package managers and software repositories play a vital role in expanding software availability on Linux systems. Distributions such as Ubuntu and Fedora provide extensive repositories containing thousands of free and open-source applications that can be easily installed with just a few clicks. These repositories cover various domains including productivity tools, multimedia applications, development environments, and more.
In cases where specific proprietary software is required on a Linux system, there are workarounds available as well. Virtualization technologies like VirtualBox or VMware allow users to run alternative operating systems within their Linux environment. This enables access to applications that may not have native Linux support.
Moreover, compatibility layers and emulators like Wine or CrossOver can bridge the gap between Linux and certain Windows applications. While not foolproof, these tools can often provide satisfactory performance for running Windows software on a Linux system.
It is also worth mentioning that the limited software availability conundrum in Linux has significantly improved over the years. As the popularity of Linux continues to grow, more developers are recognizing its potential and actively working towards providing native support for their software.
In conclusion, while it is true that Linux systems may not have direct compatibility with all popular programs and applications, it’s important to consider the broader context. The Linux community has made significant strides in expanding software availability through official support, open-source alternatives, package managers, virtualization technologies, and compatibility layers. With a bit of exploration and adaptability, users can find suitable solutions for their software needs within the vast ecosystem of Linux.
Lack of support – As Linux is open-source, there is no official provider of technical or customer support for the system.
Addressing the Lack of Official Support in the Linux System
One of the criticisms often raised against Linux is the perceived lack of official technical or customer support. Unlike proprietary operating systems, Linux does not have a single company or vendor that provides dedicated support services. However, it’s important to recognize that this perceived con can be mitigated by understanding the unique support ecosystem that has developed around Linux.
While there may not be a centralized entity offering official support, the Linux community itself has stepped up to fill this void. The open-source nature of Linux has fostered a vibrant and knowledgeable community of users, developers, and enthusiasts who are passionate about helping others. Online forums, discussion boards, and mailing lists provide avenues for users to seek assistance, troubleshoot issues, and find solutions.
These community-driven support channels often prove to be invaluable resources for Linux users. With countless experienced individuals willing to share their expertise and offer guidance, it’s possible to find answers to most questions or problems encountered while using Linux. The collaborative nature of these communities ensures that issues are addressed promptly and with multiple perspectives.
In addition to community support, many popular Linux distributions have established their own dedicated forums and online communities where users can seek help specific to their chosen distribution. These forums are often frequented by both knowledgeable volunteers and distribution maintainers who actively participate in discussions and provide guidance.
Furthermore, commercial entities have recognized the growing popularity of Linux and have started offering professional technical support services for businesses and organizations using Linux systems. These companies employ experts who specialize in various aspects of Linux administration and troubleshooting. They provide tailored solutions based on specific needs, ensuring prompt assistance when required.
It’s worth noting that while official paid support may not be as prevalent as with proprietary systems initially, the availability of professional services is expanding rapidly as more businesses adopt Linux as their preferred operating system.
Moreover, with its open-source nature comes an inherent advantage – transparency. The ability to access the source code allows skilled individuals to delve into the system’s inner workings, diagnose problems, and develop fixes independently. This level of transparency not only empowers users but also fosters a culture of self-reliance and knowledge sharing within the Linux community.
While it is true that Linux lacks a centralized official support provider, the absence of such does not necessarily translate to an absence of support altogether. The Linux community’s collective expertise, coupled with commercial support options and the transparency inherent in open-source software, ensures that users have access to a wide range of resources to address their needs.
Ultimately, it is this unique support ecosystem that has allowed Linux to thrive and gain widespread adoption across various industries and user groups. By embracing the collaborative spirit and leveraging available resources, users can overcome any perceived lack of official support and fully enjoy the benefits that Linux has to offer.
Complexity – The user interface can be complex and difficult for novice users to understand and navigate, requiring some basic knowledge of computers before use.
Navigating the Complexity of Linux: A Learning Curve Worth Conquering
Linux, with its myriad benefits and strengths, is not without its challenges. One of the commonly cited drawbacks is its perceived complexity, particularly when it comes to the user interface. Novice users may find themselves initially overwhelmed by the unfamiliarity and intricacy of navigating a Linux system. However, while it may require some basic knowledge of computers before diving in, the learning curve is well worth conquering.
Unlike other operating systems that prioritize simplicity and ease-of-use, Linux offers a vast array of choices and customization options. This richness in features and flexibility can lead to a steeper learning curve for those new to the system. The command-line interface (CLI), often associated with Linux, can appear daunting at first glance. It requires users to input commands manually rather than relying solely on graphical user interfaces (GUIs). This aspect can be intimidating for individuals accustomed to point-and-click interactions.
However, it’s important to note that modern Linux distributions have made significant strides in improving user-friendliness through intuitive GUIs. Popular distributions like Ubuntu and Fedora offer user-friendly interfaces that make day-to-day tasks more accessible for beginners. These distros provide graphical tools for software installation, system configuration, and file management, reducing reliance on the CLI for routine operations.
Moreover, numerous online resources are available to assist newcomers in their journey into the Linux world. Comprehensive documentation, forums, tutorials, and supportive communities exist to help answer questions and provide guidance. Embracing these resources can significantly ease the initial complexities associated with Linux.
While there may be an initial learning curve involved in understanding and navigating a Linux system, this investment of time and effort reaps significant rewards. Once users become familiar with the underlying principles of Linux and gain confidence in using its tools effectively, they unlock a world of possibilities.
Linux’s complexity ultimately empowers users by granting them greater control over their computing experience. The ability to customize and fine-tune the system to suit individual needs is a hallmark of Linux’s strength. Whether it’s tweaking system settings, optimizing performance, or delving into advanced scripting, Linux offers unparalleled flexibility for those willing to explore its depths.
Additionally, as users gain proficiency in Linux, they acquire transferable skills that can be valuable in various professional settings. Many industries rely on Linux-based systems for their stability, security, and scalability. Proficiency in Linux can open doors to career opportunities in fields such as software development, cybersecurity, data analysis, and system administration.
In conclusion, while the complexity of the Linux user interface may pose a temporary challenge for novice users, it is a hurdle that can be overcome with patience and perseverance. The rewards of embracing Linux’s power and versatility far outweigh the initial learning curve. With a wealth of resources available and an engaged community ready to assist, diving into the world of Linux holds great potential for personal growth and professional development. Embrace the challenge and unlock the endless possibilities that await within the realm of Linux.
Security risks – Although Linux systems have a good reputation for security, they are still vulnerable to viruses and malware if not kept up-to-date with patches and security updates.
Addressing Security Risks in Linux Systems
Linux systems have long been lauded for their robust security measures, but it’s important to acknowledge that no operating system is entirely immune to security risks. While Linux enjoys a reputation for being more secure than its counterparts, it is not impervious to viruses and malware if proper precautions are not taken.
One potential vulnerability lies in outdated software. Like any operating system, Linux relies on regular updates and patches to address newly discovered vulnerabilities and enhance security measures. Failure to keep the system up-to-date with the latest patches can leave it exposed to potential threats. Therefore, it is crucial for users to diligently install security updates and stay informed about any known vulnerabilities.
Another factor that can contribute to security risks in Linux systems is user error or negligence. Even with strong built-in security features, users must exercise caution when installing third-party software or visiting potentially malicious websites. Careless behavior such as downloading files from untrusted sources or clicking on suspicious links can expose the system to malware infections.
Additionally, while Linux has a smaller market share compared to other operating systems, it does not make it immune to targeted attacks. As its popularity continues to grow, so does the interest of hackers seeking vulnerabilities within Linux systems. It is essential for users to remain vigilant and employ best practices such as using strong passwords, implementing firewalls, and employing additional security tools when necessary.
Fortunately, the Linux community is well-aware of these potential risks and actively works towards mitigating them. The open-source nature of Linux allows for rapid identification and patching of vulnerabilities by a vast community of developers worldwide. This means that once a vulnerability is discovered, fixes are often released promptly.
Moreover, many popular Linux distributions provide robust package management systems that simplify the process of updating software packages and applying security patches. These tools help streamline the maintenance process and ensure that users have access to the latest security updates effortlessly.
In conclusion, while Linux systems are generally regarded as more secure, it is crucial to address the potential security risks they may face. By staying proactive and adhering to best practices such as regularly updating software, exercising caution while browsing the internet, and utilizing additional security tools when necessary, users can significantly enhance the security of their Linux systems. With a vigilant approach, Linux users can continue to enjoy the benefits of this powerful and versatile operating system while minimizing potential security threats.
Hardware compatibility issues – Not all hardware components are compatible with Linux systems, so it’s important to check this before installation or purchase new components specifically designed for the system.
Navigating Hardware Compatibility Issues in Linux Systems
While Linux boasts numerous advantages, it’s important to acknowledge that it faces some challenges as well. One notable drawback is the potential for hardware compatibility issues. Unlike mainstream operating systems like Windows and macOS, not all hardware components are guaranteed to be compatible with Linux systems. This can pose a hurdle for users, requiring them to carefully consider hardware compatibility before installation or purchasing new components.
One of the primary reasons for these compatibility issues is the closed nature of many hardware manufacturers. They often design their products with proprietary drivers that are tailored exclusively for popular operating systems like Windows. As a result, Linux users may encounter difficulties when attempting to use certain devices or peripherals.
However, it’s crucial to note that the situation has improved significantly over the years. The Linux community has made tremendous strides in developing open-source drivers and collaborating with hardware manufacturers to ensure better compatibility. Many manufacturers now provide Linux-friendly drivers or release specifications that allow developers to create open-source drivers.
To mitigate potential compatibility problems, it is advisable to research and choose hardware components known for their Linux compatibility. Various online resources and forums provide information on specific devices and their compatibility with different Linux distributions. Checking these sources before making a purchase can save users from later frustration.
Another helpful approach is to opt for well-established Linux-friendly hardware brands or models that have been extensively tested by the community. These devices tend to have better support from both the manufacturer and the open-source community, ensuring a smoother experience during installation and usage.
Additionally, when encountering compatibility issues, there are often workarounds available within the Linux ecosystem. The vast community of Linux users and developers offers support through forums, wikis, and dedicated websites where individuals share their experiences and solutions for various hardware-related challenges.
It’s worth noting that while some hardware components may not have native support on Linux systems, there are often alternative solutions available. For example, if a specific wireless network card lacks Linux drivers, there may be compatible USB adapters or other workarounds that can be used instead. Exploring these alternatives can help users find suitable solutions for their hardware needs.
In conclusion, while hardware compatibility issues are a potential con of Linux systems, the situation has significantly improved over time. The Linux community’s dedication and collaboration with hardware manufacturers have led to better support and compatibility. By conducting thorough research, choosing Linux-friendly hardware, and seeking assistance from the community when needed, users can navigate these challenges effectively and enjoy the many benefits that Linux offers as an open-source operating system.