Elevate Your Career with Linux Certification Programs: Unlocking Opportunities in the World of Open-Source
Linux Certification Programs: Unlocking Opportunities in the World of Open-Source
In today’s technology-driven world, Linux has emerged as a powerful and widely adopted operating system. Known for its stability, security, and versatility, Linux is the backbone of countless servers, supercomputers, mobile devices, and embedded systems. As the demand for Linux expertise continues to grow, obtaining a Linux certification can provide individuals with a competitive edge and open doors to exciting career opportunities.
Linux certification programs are designed to validate an individual’s knowledge and skills in various aspects of Linux administration and development. These programs offer a structured curriculum that covers essential topics such as system administration, networking, security, scripting, and more. By earning a Linux certification, professionals demonstrate their proficiency in working with this popular open-source platform.
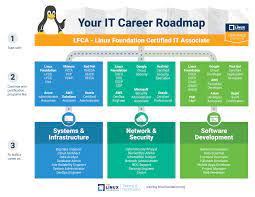
One of the most recognized Linux certification programs is the Linux Professional Institute (LPI) Certification. LPI offers multiple levels of certification that cater to different skill levels – from entry-level sysadmins to seasoned professionals. The LPI certifications are vendor-neutral, meaning they focus on core skills applicable across different distributions of Linux. This ensures that certified individuals possess a broad understanding of Linux principles rather than being limited to a specific distribution.
Another well-regarded certification program is offered by Red Hat – the Red Hat Certified Engineer (RHCE) program. Red Hat is one of the leading contributors to the development of enterprise-grade Linux distributions. The RHCE program focuses on advanced system administration skills specifically tailored for Red Hat Enterprise Linux (RHEL). With an RHCE certification in hand, professionals demonstrate their ability to manage complex systems using Red Hat technologies.
Other notable certifications include those offered by CompTIA (such as CompTIA Linux+), SUSE (SUSE Certified Administrator), and Ubuntu (Ubuntu Certified Professional). Each program has its own unique curriculum and emphasis but shares the common goal of validating an individual’s expertise in working with Linux.
So why should you consider pursuing a Linux certification? Firstly, it provides a tangible proof of your skills and knowledge in Linux administration or development. Employers often look for certified professionals as it gives them confidence in the candidate’s abilities. Secondly, a Linux certification can enhance your career prospects by opening doors to job opportunities that specifically require Linux expertise. Many organizations, especially those in the IT industry, rely heavily on Linux systems and actively seek certified professionals to manage their infrastructure. Lastly, obtaining a Linux certification allows you to stay updated with the latest industry standards and best practices, ensuring that your skills remain relevant and competitive.
Preparing for a Linux certification exam requires dedication and commitment. It involves studying relevant topics, practicing hands-on exercises, and familiarizing yourself with various tools and commands used in Linux administration or development. Fortunately, there are numerous resources available to help you prepare, including official study guides, online courses, practice exams, and community forums where you can interact with fellow learners.
In conclusion, Linux certification programs offer individuals an opportunity to validate their skills and enhance their career prospects in the world of open-source technology. Whether you are an aspiring system administrator or a seasoned IT professional looking to specialize in Linux, earning a Linux certification can provide you with the recognition and credibility needed to succeed in this ever-evolving field. So take the leap today and unlock new possibilities with a Linux certification!
Frequently Asked Questions about Linux Certification Programs in the UK
- What is the best Linux certification program?
- How much does a Linux certification cost?
- How long does it take to get certified in Linux?
- What are the benefits of getting a Linux certification?
- Are there any free online resources for learning Linux to help me prepare for certification exams?
What is the best Linux certification program?
Determining the “best” Linux certification program depends on various factors, including your career goals, experience level, and specific areas of interest within the Linux ecosystem. However, several widely recognized and respected Linux certification programs are worth considering:
- Linux Professional Institute (LPI) Certification: LPI offers a vendor-neutral certification program that covers essential Linux skills applicable across different distributions. LPI certifications are highly regarded in the industry and cater to various skill levels, from entry-level to advanced.
- Red Hat Certified Engineer (RHCE): Offered by Red Hat, this certification focuses on advanced system administration skills specific to Red Hat Enterprise Linux (RHEL). RHCE is particularly valuable if you intend to work with RHEL or in organizations that heavily rely on Red Hat technologies.
- CompTIA Linux+: This certification program provided by CompTIA is vendor-neutral and covers a wide range of foundational Linux skills. It is an excellent starting point for individuals new to Linux and seeking a comprehensive understanding of its fundamentals.
- SUSE Certified Administrator: If you plan to work with SUSE Linux Enterprise Server (SLES), obtaining this certification demonstrates your proficiency in managing SUSE-based systems. It validates your expertise in SLES administration, deployment, and troubleshooting.
- Ubuntu Certified Professional: Offered by Canonical, this certification focuses on Ubuntu Server administration skills. It is beneficial if you aim to work with Ubuntu-based systems or organizations that primarily use Ubuntu as their preferred distribution.
Ultimately, the best Linux certification program for you depends on your specific career aspirations and the direction you want to take within the Linux ecosystem. Consider factors such as industry demand, job requirements in your desired field, personal interests, and future growth opportunities when making your decision.
How much does a Linux certification cost?
The cost of Linux certification varies depending on the certification program and the level of certification you are pursuing. Generally, Linux certification exams range in price from around $150 to $500.
For example, the Linux Professional Institute (LPI) offers different levels of certification, with exam fees typically ranging from $188 to $226 per exam. Red Hat certifications, such as the Red Hat Certified Engineer (RHCE), have exam fees that can range from $400 to $600.
It’s important to note that these prices are subject to change and may vary based on factors such as your location and any additional study materials or training courses you choose to invest in. Some certification programs also offer bundle packages that include multiple exams or study resources at a discounted rate.
Before registering for a Linux certification exam, it’s recommended to visit the official website of the respective certification program to get accurate and up-to-date pricing information. Additionally, keep in mind that there may be additional costs involved if you choose to pursue training courses or study materials to help you prepare for the exams.
How long does it take to get certified in Linux?
The time it takes to get certified in Linux can vary depending on several factors, including the level of certification you aim to achieve, your prior experience and knowledge of Linux, and the amount of time you can dedicate to studying and preparation.
For entry-level certifications, such as the CompTIA Linux+ or LPI Linux Essentials, it may take a few months of consistent study and practice to adequately prepare. These certifications typically require a foundational understanding of Linux concepts and basic administration tasks.
For more advanced certifications like the LPI LPIC-1 or Red Hat Certified System Administrator (RHCSA), it may take several months of focused study and hands-on practice. These certifications delve deeper into system administration skills and often require a higher level of proficiency in working with Linux systems.
The time required to prepare for higher-level certifications, such as the LPI LPIC-2 or Red Hat Certified Engineer (RHCE), can vary greatly depending on your existing knowledge and experience. These certifications typically demand a broader range of advanced skills and may require more extensive study and practical experience.
It’s important to note that everyone learns at their own pace, so the duration mentioned above is just an estimate. Some individuals may be able to complete their studies and pass the exams in a shorter timeframe, while others may require more time.
To maximize your chances of success, it’s recommended to create a study plan that includes regular study sessions, hands-on practice with Linux systems, review of relevant materials (such as official study guides or online courses), and taking advantage of practice exams for self-assessment.
Remember that certification is not just about passing an exam but also gaining practical knowledge and skills. So it’s crucial to allocate enough time for hands-on practice in real-world scenarios to reinforce your understanding of Linux concepts.
Ultimately, the time it takes to get certified in Linux will depend on your dedication, prior knowledge, available resources, and individual learning style. By setting realistic goals, staying consistent with your studies, and actively engaging with the material, you can work towards obtaining your Linux certification within a reasonable timeframe.
What are the benefits of getting a Linux certification?
Obtaining a Linux certification offers numerous benefits that can positively impact your career and professional growth. Here are some key advantages of getting a Linux certification:
- Enhanced Career Opportunities: Linux is widely used in various industries, including IT, software development, cybersecurity, cloud computing, and more. Having a Linux certification can significantly expand your job prospects and make you a desirable candidate for positions that specifically require Linux expertise. It demonstrates to employers that you possess the necessary skills to manage and administer Linux systems effectively.
- Validation of Skills: A Linux certification serves as tangible proof of your knowledge and proficiency in working with Linux. It validates your understanding of core concepts, tools, commands, and best practices related to system administration or development on the Linux platform. This validation can boost your confidence and provide reassurance to employers about your capabilities.
- Credibility and Trust: Employers often value certifications from reputable organizations as they indicate a certain level of competence and dedication to professional growth. By earning a recognized Linux certification, you establish credibility within the industry and gain the trust of employers who rely on certified professionals to handle critical systems.
- Competitive Edge: In a competitive job market, having a Linux certification sets you apart from other candidates who may not have formal training or credentials in Linux administration or development. It demonstrates your commitment to continuous learning and staying updated with industry standards, giving you an edge over others vying for similar positions.
- Industry Recognition: Reputable Linux certifications are recognized globally by industry professionals, organizations, and peers alike. They carry weight when it comes to assessing technical skills and expertise in the field of open-source technology. Being certified can help you gain recognition within the community and open doors for networking opportunities.
- Skill Development: Preparing for a Linux certification exam requires comprehensive study and practical hands-on experience with various aspects of Linux administration or development. This process helps you deepen your understanding of the operating system, sharpen your problem-solving abilities, and expand your knowledge of Linux tools and technologies. This skill development can benefit you in your current role or future endeavors.
- Continued Professional Growth: Linux certifications often require candidates to stay updated with the latest advancements and changes in the Linux ecosystem. This encourages continuous learning and professional growth as you strive to maintain your certification status. By staying current with industry trends, you can adapt to evolving technologies and remain relevant in the ever-changing IT landscape.
In summary, obtaining a Linux certification offers a range of benefits, including increased career opportunities, validation of skills, enhanced credibility, a competitive edge in the job market, industry recognition, skill development, and continued professional growth. Whether you are starting your career or looking to advance in the field of open-source technology, a Linux certification can be a valuable asset that opens doors to exciting opportunities.
Are there any free online resources for learning Linux to help me prepare for certification exams?
Absolutely! There are several free online resources available to help you learn Linux and prepare for certification exams. Here are a few popular ones:
- Linux Academy Community Edition: Linux Academy offers a free community edition that provides access to a wide range of Linux courses, hands-on labs, and study materials. While the full membership is paid, the community edition offers a selection of free content that can be incredibly useful for learning and exam preparation.
- edX: This platform offers various Linux-related courses from reputable institutions such as The Linux Foundation. Courses like “Introduction to Linux” provide a solid foundation, while more advanced courses cover topics like system administration and networking.
- FreeCodeCamp: FreeCodeCamp is known for its programming curriculum, but it also offers free tutorials on Linux essentials. These tutorials cover the basics of using the command line, file management, and more.
- The Linux Documentation Project (TLDP): TLDP hosts an extensive collection of guides, how-tos, and documentation related to all aspects of Linux. It’s a valuable resource for understanding different concepts and troubleshooting common issues.
- YouTube tutorials: Many YouTubers create comprehensive video tutorials on various aspects of Linux administration and development. Channels like “The Urban Penguin” or “Chris Titus Tech” offer step-by-step guides that can be helpful in learning specific topics or preparing for certification exams.
- Official distribution documentation: Each major Linux distribution has its own official documentation available online for free. For example, Ubuntu has its official documentation website (help.ubuntu.com) with comprehensive guides on installation, configuration, and usage.
- Online forums and communities: Engaging with online forums like Reddit’s r/linuxquestions or Stack Exchange’s Unix & Linux can help you get answers to specific questions or troubleshoot issues you encounter while learning.
Remember that while these resources are valuable for self-study and exam preparation, it’s also recommended to refer to the official certification exam objectives and study guides provided by the certification program you are pursuing. These resources will give you a clear understanding of what topics and skills are covered in the exam, allowing you to focus your learning efforts effectively.
By leveraging these free online resources, you can gain a solid understanding of Linux and enhance your chances of success in your certification journey. Happy learning!