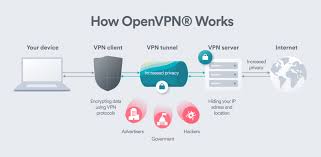
Tech Innovation: Shaping the Future
In today’s fast-paced world, technology has become an integral part of our daily lives. From smartphones and smart homes to artificial intelligence and virtual reality, tech innovation continues to revolutionize the way we live, work, and connect with others. It drives progress and opens up new possibilities that were once unimaginable. Let’s explore how tech innovation is shaping the future and transforming various aspects of our society.
One area where tech innovation has had a profound impact is communication. The advent of the internet and social media platforms has connected people from all corners of the globe, breaking down barriers and fostering a sense of global community. We can now effortlessly communicate with friends, family, and colleagues regardless of distance or time zones. Video conferencing tools have made remote work more accessible than ever before, enabling teams to collaborate seamlessly across borders.
Another field that has experienced significant transformation is healthcare. Technological advancements have paved the way for more accurate diagnoses, personalized treatments, and improved patient care. Telemedicine allows individuals to consult with healthcare professionals remotely, reducing the need for in-person visits and increasing accessibility to medical expertise. Wearable devices such as fitness trackers and smartwatches enable users to monitor their health in real-time, empowering them to make informed decisions about their well-being.
Education is another sector that has been greatly influenced by tech innovation. Online learning platforms have made education accessible to a wider audience by breaking down geographical limitations. Students can now access educational resources from renowned institutions around the world without leaving their homes. Interactive learning tools like virtual reality simulations provide immersive experiences that enhance understanding and engagement.
Transportation is yet another area where tech innovation is reshaping our lives. Electric vehicles are becoming increasingly popular as society seeks greener alternatives to traditional petrol-powered cars. Self-driving cars are on the horizon, promising safer roads by eliminating human error from driving equations. Ride-sharing services have revolutionized urban mobility by providing convenient and cost-effective transportation options.
Innovation in technology has also transformed the business landscape. Start-ups and entrepreneurs are leveraging advancements in artificial intelligence, big data analytics, and cloud computing to disrupt traditional industries and create new business models. E-commerce platforms have revolutionized the way we shop, offering convenience, variety, and personalized recommendations. Blockchain technology has the potential to revolutionize industries such as finance, supply chain management, and healthcare by providing secure and transparent transactions.
However, with all these advancements come ethical considerations. As tech innovation continues to push boundaries, questions arise regarding privacy, data security, and the impact on jobs. Striking a balance between progress and ethical responsibility is crucial to ensure that tech innovation benefits society as a whole.
Tech innovation is an ongoing journey with limitless possibilities. It has the power to transform our lives for the better, making them more efficient, connected, and sustainable. Embracing these innovations while addressing their challenges will shape our future in profound ways. So let us continue to embrace tech innovation as a force for positive change and work towards a future where technology enhances our lives while maintaining our values and principles.
9 Pros of Tech Innovation: Enhancing Efficiency, Customer Experience, Cost Savings, Information Access, Security, Communication, Decision Making, Predictions, and Scalability
- Increased efficiency – Tech innovation can help to automate processes, improve accuracy and reduce manual labour time, leading to increased efficiency.
- Improved customer experience – By introducing new technologies such as AI-driven chatbots or virtual assistants, businesses can provide a more personalised and efficient service for their customers.
- Cost savings – Automation and the use of data-driven insights can help businesses reduce operational costs by streamlining processes and increasing efficiency.
- Increased access to information – New technologies such as cloud computing allow companies to store large amounts of data securely in the cloud and access it from anywhere in the world at any time.
- Enhanced security – With tech innovations such as biometric authentication systems, businesses can ensure that their data is secure from unauthorised access or manipulation.
- Improved communication – Technologies like instant messaging apps and video conferencing solutions enable businesses to communicate with employees, customers or partners quickly and easily, regardless of location or device type used.
- Faster decision making – By using predictive analytics tools powered by artificial intelligence (AI) algorithms , companies can make faster decisions based on real-time data insights .
- More accurate predictions – AI-enabled systems are able to analyse large amounts of data quickly , helping organisations make better predictions about future trends .
- Greater scalability – Cloud computing solutions allow organisations to scale up their operations without needing additional hardware investments , enabling them to expand quickly when needed .
Unveiling the Dark Side: 6 Cons of Tech Innovation in the UK
- It can lead to job losses, as automation and artificial intelligence become more prevalent.
- It can create a digital divide between those who have access to the latest technology and those who don’t.
- It can lead to increased surveillance of citizens by governments and corporations, reducing privacy rights.
- It can increase inequality, as those with the resources to invest in tech innovation benefit most from it while others are left behind.
- There is a risk that tech innovation could be used for malicious purposes such as cyber attacks or data theft.
- Tech innovation can be expensive and complex, meaning small businesses may struggle to keep up with the latest developments in technology
Increased efficiency – Tech innovation can help to automate processes, improve accuracy and reduce manual labour time, leading to increased efficiency.
Increased Efficiency: The Power of Tech Innovation
In today’s fast-paced world, efficiency is key to success. Businesses and individuals alike are constantly seeking ways to streamline processes, reduce manual labour, and improve accuracy. This is where tech innovation comes into play, offering a range of solutions that can significantly boost efficiency across various sectors.
One major advantage of tech innovation is its ability to automate processes. Repetitive and time-consuming tasks can be automated using advanced software and robotics, freeing up valuable time for employees to focus on more strategic and creative aspects of their work. This not only increases productivity but also reduces the risk of human error, leading to improved accuracy in operations.
Take, for example, the manufacturing industry. With the introduction of technologies such as robotics and machine learning, production lines can now operate with minimal human intervention. This not only speeds up the manufacturing process but also ensures consistent quality control. By automating repetitive tasks, companies can achieve higher output levels while maintaining high standards.
Tech innovation also plays a significant role in improving efficiency in data management and analysis. With the advent of big data analytics tools, businesses can now process vast amounts of information in real-time. This allows for better decision-making based on accurate insights and trends. Manual data entry and analysis that would have taken hours or even days can now be completed within minutes or seconds.
In addition to automation and data management, tech innovation has revolutionized communication channels. The rise of digital platforms has made it easier than ever to collaborate remotely with colleagues or clients from different parts of the world. Video conferencing tools, project management software, and instant messaging platforms enable real-time communication and seamless collaboration across teams.
Moreover, cloud computing has transformed the way businesses store and access their data. Cloud-based solutions offer scalable storage options that eliminate the need for physical servers or extensive IT infrastructure maintenance. This not only saves costs but also provides increased flexibility and accessibility to data from anywhere at any time.
By reducing manual labour time and improving accuracy, tech innovation allows businesses to operate more efficiently. This increased efficiency translates into cost savings, improved customer satisfaction, and a competitive edge in the market. Moreover, it frees up resources that can be redirected towards innovation and growth.
However, it is important to note that tech innovation should be implemented thoughtfully and with consideration for potential challenges. It is crucial to ensure that employees are properly trained to adapt to new technologies and that any potential ethical concerns are addressed.
In conclusion, tech innovation has proven to be a game-changer when it comes to increasing efficiency. By automating processes, improving accuracy, and reducing manual labour time, businesses can unlock their full potential and achieve higher levels of productivity. Embracing tech innovation not only benefits individual organizations but also contributes to overall economic growth and progress. So let us embrace the power of tech innovation as we strive for a more efficient future.
Improved customer experience – By introducing new technologies such as AI-driven chatbots or virtual assistants, businesses can provide a more personalised and efficient service for their customers.
Improved Customer Experience: Personalized and Efficient Service through Tech Innovation
In today’s competitive business landscape, customer experience plays a pivotal role in shaping brand loyalty and success. With the advent of technology, businesses have been able to harness its power to enhance customer experiences like never before. One significant pro of tech innovation is the ability to provide a more personalized and efficient service for customers through the introduction of new technologies such as AI-driven chatbots or virtual assistants.
One key advantage of these technologies is their ability to offer personalized interactions with customers. AI-driven chatbots, for example, can analyze customer data and preferences to provide tailored recommendations or solutions. By understanding customer needs and preferences, businesses can deliver targeted assistance, making customers feel valued and understood. This personalization helps foster a stronger connection between businesses and their customers.
Tech innovation also enables businesses to provide round-the-clock support through virtual assistants or chatbots. Customers no longer have to wait for office hours or navigate complex phone menus to get assistance. AI-powered systems can handle a wide range of queries efficiently and effectively, providing instant responses and resolving issues promptly. This 24/7 availability ensures that customers receive the support they need whenever they require it, leading to increased satisfaction and loyalty.
Moreover, these technologies streamline customer interactions by automating routine tasks. Virtual assistants can handle basic inquiries, process transactions, or guide customers through simple procedures, freeing up human agents’ time for more complex or specialized tasks. This automation not only improves efficiency but also reduces waiting times for customers, resulting in a smoother and more seamless experience.
Additionally, tech innovation allows businesses to gather valuable insights about their customers’ preferences and behaviors. By analyzing data collected from interactions with chatbots or virtual assistants, companies can gain a deeper understanding of their target audience. These insights can be used to refine marketing strategies, personalize offers, and improve product development based on real-time feedback from customers.
Ultimately, by leveraging new technologies, businesses can elevate the customer experience to new heights. Personalized interactions, round-the-clock support, and streamlined processes all contribute to a more satisfying and efficient service. Customers feel valued and appreciated when their needs are met promptly and accurately, leading to increased loyalty and positive word-of-mouth recommendations.
As tech innovation continues to evolve, businesses must embrace these advancements to stay competitive in the modern marketplace. By investing in AI-driven chatbots or virtual assistants, companies can enhance their customer experience, build stronger relationships with their clientele, and ultimately drive growth and success.
In conclusion, improved customer experience through tech innovation is a significant pro that benefits both businesses and customers alike. By leveraging AI-driven technologies, companies can provide personalized interactions, efficient support, and streamlined processes that leave a lasting impression on customers. Embracing these innovations is key to staying ahead in today’s digital era where exceptional customer service sets businesses apart from the competition.
Cost savings – Automation and the use of data-driven insights can help businesses reduce operational costs by streamlining processes and increasing efficiency.
Cost Savings: Streamlining Business Operations through Tech Innovation
In today’s competitive business landscape, finding ways to reduce operational costs is a top priority for organizations of all sizes. One significant advantage that tech innovation brings to the table is the ability to streamline processes and increase efficiency, leading to substantial cost savings. Through automation and data-driven insights, businesses can optimize their operations and achieve financial benefits.
Automation plays a pivotal role in driving cost savings. By automating repetitive tasks, businesses can free up valuable time and resources that can be redirected towards more strategic initiatives. Manual processes are not only time-consuming but also prone to errors. With automation, businesses can minimize human error and improve accuracy, leading to fewer costly mistakes. This not only saves money but also enhances overall productivity.
Furthermore, automation reduces the need for extensive manpower in certain areas of operations. By leveraging technology solutions such as robotic process automation (RPA) or artificial intelligence (AI), businesses can streamline workflows and eliminate the need for manual intervention. This reduction in labor costs can significantly contribute to overall cost savings while ensuring consistent and reliable results.
Data-driven insights are another powerful tool that tech innovation brings to the table. With the abundance of data available today, businesses can harness this information to gain valuable insights into their operations. By analyzing data patterns and trends, organizations can identify inefficiencies or bottlenecks within their processes. Armed with this knowledge, they can make informed decisions on how best to optimize their operations, thereby reducing costs.
For example, data analytics can help identify areas where resources are being underutilized or where unnecessary expenses are occurring. By understanding these patterns, businesses can make adjustments that lead to better resource allocation and cost optimization. Additionally, data-driven insights enable organizations to anticipate customer demands more accurately, allowing for efficient inventory management and reducing wastage or overstocking.
Tech innovation also enables real-time monitoring and tracking of key performance indicators (KPIs). Businesses can use dashboards and analytics tools to gain a comprehensive view of their operations, enabling them to identify areas that are performing below expectations. This visibility allows for timely interventions and corrective measures, preventing potential losses and maximizing efficiency.
In summary, tech innovation offers businesses the opportunity to achieve substantial cost savings through automation and data-driven insights. By automating repetitive tasks, organizations can reduce errors, increase productivity, and optimize resource allocation. Data analysis provides valuable insights that help identify inefficiencies and enable informed decision-making for cost optimization. Embracing tech innovation not only enhances operational efficiency but also contributes to overall financial success in today’s competitive business environment.
Increased Access to Information: Empowering the World
In today’s digital age, information is power. The ability to access and retrieve data quickly and efficiently has become a vital component of success for businesses and individuals alike. Thanks to tech innovation, specifically advancements in cloud computing, the world is witnessing a remarkable transformation in the way information is stored, managed, and accessed.
Cloud computing has revolutionized the way companies store their data. Traditionally, businesses had to rely on physical servers and infrastructure to store their information. This not only required significant investment but also posed challenges in terms of scalability and accessibility. However, with the advent of cloud computing technology, companies can now securely store vast amounts of data in remote servers maintained by third-party providers.
One of the key advantages of cloud computing is the increased accessibility it offers. Companies no longer need to be tied down to a specific physical location or worry about the limitations of local storage capacity. With data stored securely in the cloud, employees can access it from anywhere in the world at any time using an internet connection. This flexibility allows for seamless collaboration among teams spread across different locations or even continents.
The benefits extend beyond just businesses. Cloud computing has also opened up new opportunities for individuals to access information like never before. With cloud-based storage services readily available, people can effortlessly back up their personal files such as photos, documents, and videos without relying on physical storage devices that are prone to loss or damage. Additionally, cloud-based productivity tools enable users to work on documents or projects collaboratively with others in real-time.
The increased access to information provided by cloud computing has also had a profound impact on education and research fields. Students can now access educational resources online from anywhere around the globe, breaking down geographical barriers that once limited learning opportunities. Researchers can collaborate more effectively by sharing large datasets through secure cloud platforms, accelerating scientific discoveries and innovation.
Furthermore, this enhanced accessibility has proven invaluable during times of crisis. In the face of natural disasters or unforeseen events, cloud-based systems ensure that critical data remains safe and accessible. This has been particularly evident in recent times with remote work becoming the norm. Cloud computing has enabled businesses to seamlessly transition to remote operations, allowing employees to access vital information and continue their work without disruption.
However, as with any technological advancement, it is important to address concerns regarding data security and privacy. Companies must prioritize implementing robust security measures and adhere to strict protocols to protect sensitive information stored in the cloud. Additionally, governments and organizations should work together to establish regulations that ensure responsible data handling practices.
Increased access to information through cloud computing is empowering individuals and businesses across the globe. The ability to store and retrieve data securely from anywhere at any time has transformed the way we work, learn, collaborate, and innovate. As technology continues to evolve, we can expect even greater advancements in cloud computing that will further revolutionize our access to information and drive us towards a more connected and knowledge-driven world.
Enhanced security – With tech innovations such as biometric authentication systems, businesses can ensure that their data is secure from unauthorised access or manipulation.
Enhanced Security: Safeguarding Data in the Digital Age
In an era where data breaches and cyber threats are prevalent, ensuring the security of sensitive information has become a top priority for businesses. Fortunately, tech innovation has brought forth significant advancements in the field of security, providing robust solutions to protect valuable data from unauthorized access or manipulation. One such pro of tech innovation is the implementation of biometric authentication systems, which offer enhanced security measures that go beyond traditional password-based systems.
Biometric authentication systems leverage unique physical or behavioral characteristics of individuals to verify their identity. These characteristics can include fingerprints, facial recognition, iris scans, voice patterns, or even typing patterns. By utilizing these biometric markers, businesses can establish a highly secure and reliable method for granting access to sensitive data or restricted areas.
One major advantage of biometric authentication systems is their inherent difficulty to replicate or forge. Unlike passwords or PINs that can be easily forgotten, stolen, or hacked through various means, biometric traits are unique to each individual and cannot be easily replicated. This significantly reduces the risk of unauthorized access as it becomes nearly impossible for an imposter to mimic someone’s fingerprints or facial features accurately.
Moreover, biometric authentication systems provide an added layer of convenience for users. Gone are the days of remembering complex passwords or carrying around access cards. With biometrics, individuals simply need to present their unique physical or behavioral characteristic for verification purposes. This not only saves time but also eliminates the hassle associated with managing multiple passwords or access cards.
For businesses handling sensitive customer data or proprietary information, the implementation of biometric authentication systems offers peace of mind. It ensures that only authorized personnel can gain access to critical resources and minimizes the risk of data breaches caused by weak passwords or stolen credentials.
It is worth noting that while biometric authentication systems offer enhanced security measures, they also raise concerns regarding privacy and data protection. Businesses must adhere to strict guidelines and regulations to ensure the responsible and ethical use of biometric data. Transparency and consent from individuals are vital when implementing such systems to maintain trust and respect privacy rights.
In conclusion, tech innovation has brought forth significant advancements in the realm of security, with biometric authentication systems leading the way. By leveraging unique physical or behavioral characteristics, businesses can establish highly secure access control measures, safeguarding their valuable data from unauthorized access or manipulation. While enjoying enhanced security, it is crucial for businesses to prioritize privacy and adhere to ethical practices when implementing biometric authentication systems. With these measures in place, businesses can confidently protect their sensitive information in the digital age.
Improved communication – Technologies like instant messaging apps and video conferencing solutions enable businesses to communicate with employees, customers or partners quickly and easily, regardless of location or device type used.
Improved Communication: Bridging the Distance
In today’s interconnected world, communication is key to success in both personal and professional spheres. Thanks to tech innovation, we now have a multitude of tools and platforms that have revolutionized the way we communicate. Instant messaging apps and video conferencing solutions are among the standout innovations that have significantly improved communication, transcending geographical boundaries and device limitations.
Gone are the days when businesses had to rely solely on traditional methods of communication, such as phone calls or face-to-face meetings. With the advent of instant messaging apps, teams can now connect instantly, regardless of their physical location. Whether it’s a quick question or a detailed discussion, these apps provide a convenient and efficient channel for real-time communication. Colleagues can collaborate seamlessly, sharing information and ideas without delay.
Furthermore, video conferencing solutions have taken remote collaboration to a whole new level. Businesses can now conduct virtual meetings with employees, customers, or partners located anywhere in the world. These solutions not only save time and money spent on travel but also foster closer relationships by allowing participants to see each other’s facial expressions and body language. This human touch enhances understanding and builds trust even when physical proximity is not possible.
The flexibility offered by these tech innovations is invaluable in today’s globalized business landscape. Employees can work from different time zones or remote locations without sacrificing effective communication with their colleagues or clients. This has opened up new possibilities for businesses to expand their reach beyond local markets and tap into talent pools worldwide.
Moreover, improved communication technologies have also benefited customer service interactions. Businesses can now interact with their customers in real-time through various channels like live chat or instant messaging apps. This enables quick responses to inquiries or issues raised by customers, enhancing overall customer satisfaction.
It is worth noting that these advancements in communication technology have become even more significant in recent times due to the COVID-19 pandemic. With social distancing measures in place, businesses have had to rely heavily on these tools to maintain operations and ensure uninterrupted communication.
However, it is important to strike a balance between virtual communication and face-to-face interactions. While tech innovation has undoubtedly improved communication, the value of in-person connections should not be underestimated. Building personal relationships and fostering a sense of camaraderie often requires physical presence. Therefore, it is crucial to find the right blend of virtual and physical interactions to ensure effective communication across all fronts.
In conclusion, tech innovation has transformed the way we communicate, making it faster, more efficient, and more inclusive. Instant messaging apps and video conferencing solutions have bridged the distance between people and enabled seamless communication regardless of location or device used. These advancements have not only benefited businesses but also enhanced customer experiences. As we continue to embrace these innovations, it is essential to strike a balance that leverages technology while recognizing the value of personal connections.
In the fast-paced world of business, the ability to make decisions quickly and accurately is essential for success. Fortunately, technology innovation has enabled companies to do just that with predictive analytics tools powered by artificial intelligence (AI) algorithms.
These tools are able to crunch data from all sources in real-time and provide insights that can be used to make decisions quickly and accurately. This is especially useful in industries where there is a need for fast decision making such as finance, retail, and healthcare. For example, predictive analytics tools can help financial institutions make decisions about loan approvals or stock market investments in a fraction of the time it would take manually.
AI algorithms also have the potential to improve decision making accuracy by providing deeper insights into customer preferences and behaviors. This could lead to more targeted marketing campaigns and better customer service experiences.
Overall, predictive analytics tools powered by AI algorithms are revolutionizing decision making processes within businesses. Companies are now able to make faster decisions based on real-time data insights which can give them a competitive edge in their respective industries.
More accurate predictions – AI-enabled systems are able to analyse large amounts of data quickly , helping organisations make better predictions about future trends .
The world of technology is constantly evolving and innovating, providing organisations with a wealth of options to improve their operations. One such pro of tech innovation is the use of AI-enabled systems to make more accurate predictions about future trends.
Using AI-enabled systems, organisations can analyse large amounts of data quickly and accurately. This helps them to make better decisions based on the insights they gain from the data. AI-enabled systems are able to identify patterns in data that humans may not be able to detect, allowing organisations to gain a better understanding of their customers’ needs and preferences. This knowledge can then be used to make more informed decisions about how best to meet those needs and preferences.
The use of AI-enabled systems also allows organisations to forecast future trends more accurately. By analysing past trends, these systems can provide an indication of what may happen in the future, allowing organisations to plan ahead and be better prepared for any potential changes.
In summary, using AI-enabled systems helps organisations make more accurate predictions about future trends which can help them better understand their customers’ needs and preferences as well as plan ahead for any potential changes in the market. Ultimately, this leads to improved customer satisfaction and increased success for the organisation.
Greater scalability – Cloud computing solutions allow organisations to scale up their operations without needing additional hardware investments , enabling them to expand quickly when needed .
Greater Scalability: Unlocking New Possibilities with Cloud Computing
In the ever-evolving digital landscape, organisations face the constant challenge of scaling their operations to meet growing demands. This is where tech innovation, particularly cloud computing solutions, comes to the rescue. One significant advantage of tech innovation in this realm is greater scalability, enabling businesses to expand quickly and efficiently without the need for substantial hardware investments.
Traditionally, scaling up operations meant procuring additional physical infrastructure such as servers, storage devices, and networking equipment. This process was not only time-consuming but also required significant financial resources. However, with the advent of cloud computing, scalability has taken on a whole new meaning.
Cloud computing offers a flexible and scalable solution that allows businesses to increase their capacity as needed without the burden of upfront hardware costs. By leveraging cloud-based services provided by reputable providers, organisations can easily adjust their resources to match demand fluctuations. Whether it’s a sudden surge in website traffic or the need for additional storage space for data-intensive applications, cloud computing provides a seamless solution.
The beauty of cloud scalability lies in its ability to scale both vertically and horizontally. Vertical scaling involves increasing the resources allocated to an individual server or virtual machine, allowing it to handle more workload efficiently. On the other hand, horizontal scaling involves adding more servers or instances to distribute the workload across multiple resources. Both approaches offer flexibility and enable organisations to respond quickly to changing needs.
The benefits of greater scalability extend beyond just meeting immediate demands. It also enables businesses to experiment and innovate without fear of resource constraints. Start-ups and small businesses can now compete on a level playing field with established players by leveraging scalable cloud solutions that allow them to grow rapidly when opportunities arise.
Additionally, greater scalability fosters business continuity by ensuring uninterrupted service availability during peak periods or unexpected surges in demand. Cloud-based solutions are designed with redundancy and failover mechanisms that provide high availability even in challenging situations. This resilience allows organisations to maintain a seamless customer experience and avoid potential revenue losses.
Furthermore, the scalability offered by cloud computing aligns perfectly with the evolving needs of modern businesses. As technology continues to advance at an unprecedented pace, organisations must be agile and adaptable. Cloud-based solutions empower businesses to respond swiftly to market changes, seize new opportunities, and scale their operations accordingly.
In conclusion, the greater scalability provided by cloud computing is a game-changer for businesses of all sizes. It eliminates the need for significant hardware investments while enabling rapid expansion when needed. This pro of tech innovation unlocks new possibilities and empowers organisations to embrace growth without being limited by resource constraints. With cloud scalability, businesses can confidently navigate the ever-changing digital landscape and stay ahead in today’s competitive world.
It can lead to job losses, as automation and artificial intelligence become more prevalent.
The rise of technology has been a double-edged sword for many industries. On one hand, it has enabled businesses to become more efficient and productive, while on the other, it has led to job losses as automation and artificial intelligence become more prevalent.
In recent years, the impact of automation on the labour market has been significant. Automation has replaced many jobs that were once done by humans, leading to a decrease in the number of available jobs in certain sectors. This is particularly true in manufacturing and logistics, where robots are increasingly being used to do tasks that would previously have been done by humans.
At the same time, artificial intelligence (AI) is being used to automate processes such as customer service and data analysis, again resulting in fewer jobs available for humans. AI can also be used to make decisions that would normally require human input or judgement. This means that even highly skilled roles are at risk of being replaced by machines.
The impact of automation and AI on job losses is likely to continue in the future as technology advances. While this could lead to increased efficiency and productivity for businesses, it could also result in fewer job opportunities for people who have traditionally relied on manual labour or cognitive skills for their livelihoods. It is therefore important for governments and businesses alike to ensure that they are investing in training and education programmes that can help people adapt to this new technological landscape.
It can create a digital divide between those who have access to the latest technology and those who don’t.
The Digital Divide: Bridging the Gap in Tech Innovation
While tech innovation has undoubtedly brought about numerous benefits and advancements, it is essential to acknowledge its potential downside. One significant con of tech innovation is the creation of a digital divide, a gap that separates those who have access to the latest technology from those who do not. This divide can exacerbate existing inequalities and hinder progress towards a more inclusive society.
In today’s interconnected world, access to technology has become increasingly vital for education, employment opportunities, and participation in modern society. However, not everyone has equal access to the latest technological advancements. This digital divide can manifest in various ways: disparities in internet connectivity, limited access to devices such as computers or smartphones, or inadequate digital literacy skills.
One of the primary concerns regarding the digital divide is its impact on education. With schools increasingly relying on technology for teaching and learning, students without adequate access to devices or internet connectivity may struggle to keep up with their peers. This inequality in educational resources can perpetuate existing social disparities and hinder opportunities for upward mobility.
The digital divide also affects employment prospects. In an era where many jobs require digital skills, individuals without access to technology or training may find themselves at a disadvantage when searching for employment. This can lead to a cycle of poverty and limited economic growth within communities that lack technological infrastructure.
Furthermore, the digital divide can further isolate marginalized groups within society. Those without access to technology may find it challenging to participate fully in civic engagement, government services, or even staying connected with friends and family. As more services move online, individuals without internet access are left behind, widening the gap between those who have opportunities for personal growth and those who do not.
To address this issue and bridge the digital divide, concerted efforts are needed from governments, organizations, and communities. Initiatives should focus on improving internet infrastructure in underserved areas and providing affordable access to devices such as computers or smartphones. Additionally, digital literacy programs can empower individuals with the skills needed to navigate and utilize technology effectively.
Collaboration between public and private sectors is crucial in finding innovative solutions to bridge the digital divide. Governments can invest in infrastructure development and provide subsidies for internet access, while tech companies can contribute by offering affordable devices or creating tailored programs to enhance digital literacy.
Ultimately, bridging the digital divide is not just a matter of equal access to technology; it is about ensuring equal opportunities for all. By addressing this con of tech innovation head-on, we can work towards building a more inclusive society where everyone has the chance to benefit from the advancements brought about by technology. Let us strive for a future where no one is left behind in the ever-evolving digital landscape.
It can lead to increased surveillance of citizens by governments and corporations, reducing privacy rights.
The Dark Side of Tech Innovation: Threats to Privacy Rights
In today’s digital age, where technology is advancing at an unprecedented pace, concerns about privacy rights have become more prominent. While tech innovation has undoubtedly brought numerous benefits to society, it has also opened the door to increased surveillance of citizens by both governments and corporations. This erosion of privacy rights raises important questions about the balance between technological progress and individual freedoms.
Governments around the world have increasingly turned to advanced surveillance technologies to monitor their citizens. From closed-circuit television (CCTV) cameras on streets to facial recognition systems in public spaces, the reach of surveillance has expanded significantly. While these technologies can be useful for ensuring public safety and deterring crime, they also raise concerns about the potential abuse of power and invasion of privacy. The constant monitoring of individuals’ activities can lead to a chilling effect on personal freedoms and undermine the fundamental right to privacy.
Similarly, corporations have been collecting vast amounts of data from users through various digital platforms and services. This data is often used for targeted advertising, personalized recommendations, and improving user experiences. However, this collection and analysis of personal information can also be exploited for more intrusive purposes. The potential for data breaches or unauthorized access can expose individuals to identity theft, financial fraud, or other forms of misuse.
Furthermore, the integration of smart devices into our daily lives has further blurred the line between convenience and surveillance. Internet-connected devices such as smart speakers, wearables, and home automation systems collect data about our habits, preferences, and even our conversations within our own homes. This constant monitoring raises concerns about the level of control we have over our personal information and how it may be used without our explicit consent.
Protecting privacy rights in an era dominated by tech innovation requires a proactive approach from both individuals and regulatory bodies. It is essential for governments to establish robust legal frameworks that safeguard individuals’ right to privacy while still allowing for legitimate surveillance needs. Stricter regulations on data collection, storage, and usage can help ensure that individuals have control over their personal information and that it is not exploited for nefarious purposes.
At an individual level, being aware of the privacy implications of the technologies we use is crucial. This includes understanding privacy settings, being cautious about sharing personal information online, and regularly reviewing permissions granted to applications and services. Encouraging transparency from corporations regarding their data practices and advocating for stronger privacy protections can also contribute to safeguarding our rights in the digital realm.
Tech innovation has the potential to bring immense benefits to society, but it is vital to address its dark side – the potential erosion of privacy rights. By recognizing these concerns and taking proactive steps to protect privacy, we can strike a balance between technological progress and individual freedoms. It is through a collective effort that we can shape a future where tech innovation coexists harmoniously with robust privacy rights.
It can increase inequality, as those with the resources to invest in tech innovation benefit most from it while others are left behind.
Tech Innovation and the Inequality Conundrum
While tech innovation has undeniably brought about numerous benefits and advancements, it is important to acknowledge that it can also exacerbate existing inequalities within society. One significant con of tech innovation is its potential to widen the gap between those who have the resources to invest in it and those who do not, leaving certain individuals and communities behind.
In a world where access to technology is increasingly crucial, those with financial means can readily embrace the latest innovations, reaping the rewards of improved efficiency, connectivity, and opportunities. They can afford state-of-the-art devices, high-speed internet connections, and cutting-edge software. As a result, they are better positioned to navigate the digital landscape, access educational resources, explore job opportunities, and stay connected with others.
On the other hand, individuals or communities without adequate resources may struggle to keep up with the rapid pace of tech innovation. Limited access to technology or unreliable internet connections can hinder their ability to fully participate in the digital age. This digital divide can perpetuate existing socio-economic disparities by denying equal opportunities for education, employment prospects, and social inclusion.
Moreover, as industries undergo digital transformation driven by tech innovation, certain jobs may become obsolete or require new skill sets. This can lead to a growing disparity in employment opportunities between those who possess the necessary skills and qualifications and those who do not. The gap between technological haves and have-nots widens further as some individuals find themselves left behind in an increasingly digitized workforce.
Addressing this conundrum requires concerted efforts from governments, organizations, and communities alike. Initiatives aimed at bridging the digital divide should be prioritized to ensure that everyone has equal access to technology infrastructure and affordable internet services. Educational programs should focus on equipping individuals with digital literacy skills so they can fully participate in an increasingly tech-driven society.
Additionally, fostering an environment that promotes inclusive innovation is crucial. Encouraging diversity in tech-related fields and supporting entrepreneurship from underrepresented communities can help mitigate the inequality gap. Collaboration between public and private sectors can lead to the development of innovative solutions that address societal challenges and ensure that the benefits of tech innovation are accessible to all.
Tech innovation has the potential to be a powerful force for positive change, but it is vital to recognize its potential drawbacks. By actively working towards reducing inequality in access, skills, and opportunities, we can strive for a future where tech innovation becomes a tool for inclusivity rather than a driver of disparity. Only through collective efforts can we ensure that the benefits of tech innovation are shared by all members of society, creating a more equitable and inclusive digital world.
There is a risk that tech innovation could be used for malicious purposes such as cyber attacks or data theft.
The Dark Side of Tech Innovation: The Risk of Malicious Use
In the ever-evolving world of technology, innovation has brought about remarkable advancements that have transformed our lives in countless positive ways. However, as with any powerful tool, there is a potential dark side. One significant concern surrounding tech innovation is the risk of its exploitation for malicious purposes, such as cyber attacks and data theft.
With the rapid growth of interconnected devices and digital infrastructure, cybercriminals have found new avenues to exploit vulnerabilities and wreak havoc. The sophistication and frequency of cyber attacks continue to rise, posing significant threats to individuals, businesses, and even governments. Malicious actors may exploit weaknesses in software systems or networks to gain unauthorized access to sensitive information or disrupt critical services.
Data theft is a particularly alarming consequence of tech innovation gone wrong. As we increasingly rely on digital platforms and store vast amounts of personal information online, the risk of data breaches becomes more prominent. Cybercriminals may target databases containing personal details like names, addresses, financial information, or even medical records. This stolen data can then be used for identity theft or sold on the dark web for illicit purposes.
Moreover, tech innovation has also given rise to new forms of social engineering attacks that manipulate human psychology rather than exploiting technical vulnerabilities. Phishing scams, for example, trick unsuspecting individuals into divulging sensitive information by impersonating legitimate entities through emails or websites.
The potential consequences of these malicious acts are far-reaching. Individuals may face financial losses due to fraudulent activities carried out using their stolen data. Companies can suffer reputational damage and financial setbacks if customer trust is compromised by a data breach. Governments may experience security breaches that compromise national security or critical infrastructure.
Addressing this conundrum requires a multi-faceted approach involving technology developers, cybersecurity experts, policymakers, and individuals themselves. Tech innovators must prioritize security measures from the outset during product development cycles to minimize vulnerabilities that could be exploited. Regular software updates and patches should be implemented to address emerging threats and protect against known vulnerabilities.
Cybersecurity experts play a crucial role in identifying and mitigating risks. Their expertise is vital in designing robust security systems, conducting vulnerability assessments, and responding swiftly to emerging threats. Collaboration between the public and private sectors is essential to share information, best practices, and intelligence to stay ahead of cybercriminals.
Policymakers also have a responsibility to enact legislation that promotes cybersecurity standards, encourages information sharing, and holds malicious actors accountable for their actions. International cooperation is crucial in combating cybercrime as it transcends national boundaries.
Lastly, individuals must remain vigilant and take proactive steps to protect themselves online. Practicing good cyber hygiene by using strong passwords, being cautious of suspicious emails or links, and regularly updating software can go a long way in safeguarding personal data.
While the risk of tech innovation being used for malicious purposes exists, it should not overshadow the immense benefits that technology brings to our lives. By addressing these security concerns head-on through collaboration and vigilance, we can harness the power of tech innovation while minimizing its potential negative consequences.
Tech innovation can be expensive and complex, meaning small businesses may struggle to keep up with the latest developments in technology
The Cost and Complexity Conundrum: Tech Innovation and Small Businesses
Tech innovation has undoubtedly brought numerous benefits to businesses, but it also presents challenges, particularly for small businesses. One significant con is the cost and complexity associated with keeping up with the latest developments in technology. As technology advances at a rapid pace, small businesses often find themselves struggling to keep pace due to limited resources and expertise.
One of the primary hurdles for small businesses is the financial burden that comes with adopting new technologies. Investing in cutting-edge hardware, software, and infrastructure can be expensive, especially when considering ongoing maintenance and upgrades. Small businesses may have limited budgets, making it difficult to allocate funds towards costly tech innovations. This financial strain can hinder their ability to remain competitive in an increasingly digital world.
Moreover, the complexity of new technologies can pose a significant challenge for small businesses. Implementing and integrating complex systems requires technical expertise that may not be readily available within their limited workforce. The learning curve associated with understanding and utilizing advanced technologies can be steep, leading to additional costs for training or hiring specialized personnel. These complexities can overwhelm small business owners who already have multiple responsibilities to manage.
Another aspect that adds to the complexity is the ever-changing nature of tech innovation itself. What may be cutting-edge today might become outdated tomorrow as newer advancements emerge. This constant evolution necessitates continuous learning and adaptation, which can be particularly demanding for small businesses trying to stay up-to-date while managing day-to-day operations.
Fortunately, there are strategies that small businesses can employ to navigate these challenges effectively. Collaboration with technology partners or managed service providers can offer cost-effective solutions by providing access to expertise without the need for substantial upfront investments. Leveraging cloud-based services allows businesses to scale their technological capabilities as needed without heavy infrastructure costs.
Additionally, focusing on specific areas of technology that align with business goals and customer needs can help prioritize investments wisely. Conducting thorough research and seeking advice from industry experts can assist in identifying the most relevant and impactful technologies to adopt.
Moreover, small businesses can explore partnerships and collaborations within their industry to pool resources and share knowledge. Collaborative efforts can help overcome financial constraints while enabling access to the latest technology advancements.
While tech innovation can be expensive and complex for small businesses, it is crucial not to overlook the potential benefits that these innovations bring. They can enhance efficiency, streamline operations, expand market reach, and improve customer experiences. By carefully evaluating options, seeking support from experts, and adopting a strategic approach, small businesses can overcome these challenges and harness the power of tech innovation to drive growth and stay competitive in an ever-evolving digital landscape.