Operating System: The Backbone of Digital Systems
In the ever-evolving world of technology, the operating system (OS) stands as the fundamental software that powers our digital devices. Whether it’s a personal computer, smartphone, or even a smartwatch, an operating system serves as the backbone, enabling users to interact with their devices and run various applications seamlessly. In this article, we will explore the significance of operating systems and how they have shaped the way we use technology.
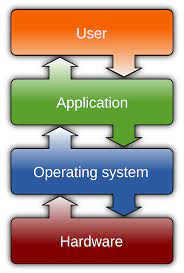
At its core, an operating system is responsible for managing hardware resources and providing a platform for software applications to run efficiently. It acts as an intermediary between users and the underlying hardware, abstracting complex functionalities into user-friendly interfaces. This abstraction allows users to interact with their devices using familiar graphical interfaces or command-line interfaces.
One of the key roles of an operating system is process management. It ensures that multiple applications can run simultaneously without interfering with each other. The OS allocates resources such as memory, CPU time, and input/output devices to different processes in a fair and efficient manner. This multitasking capability enables users to switch between applications seamlessly and increases overall productivity.
Furthermore, an operating system provides file management capabilities, allowing users to organize and access their data efficiently. It handles tasks such as creating, deleting, modifying files or directories, and ensures data integrity through file permissions and security mechanisms. Additionally, modern operating systems often include advanced file search functionalities that make it easier for users to locate specific files within their vast digital libraries.
Device drivers are another crucial component of an operating system. These drivers act as intermediaries between hardware devices (such as printers or graphics cards) and software applications. They enable communication between the two by providing a standardized interface for accessing device-specific functionalities. Without device drivers integrated into the OS, utilizing external hardware would be significantly more challenging for end-users.
Security is also a paramount concern in today’s interconnected world. Operating systems play a vital role in safeguarding users’ data and privacy. They implement various security measures such as user authentication, encryption, and access controls to protect sensitive information from unauthorized access. Operating system developers continually release security patches and updates to address vulnerabilities and ensure the safety of users’ digital assets.
The evolution of operating systems has been remarkable. From early command-line interfaces to modern graphical user interfaces (GUIs) that offer intuitive interactions, operating systems have become more user-friendly and visually appealing. Additionally, mobile operating systems have revolutionized the way we use smartphones, providing app ecosystems that cater to our every need.
Open-source operating systems like Linux have gained popularity due to their flexibility, stability, and the active communities surrounding them. These communities contribute to the development and improvement of the OS by providing feedback, bug fixes, and new features. The open-source nature fosters innovation, collaboration, and transparency within the software ecosystem.
In conclusion, operating systems are the invisible heroes behind our digital experiences. They facilitate seamless interaction between users and devices while managing resources efficiently. As technology continues to advance at an unprecedented pace, operating systems will continue to adapt and evolve to meet the changing needs of users worldwide. So next time you power up your device or swipe on your smartphone’s screen, remember that it is the operating system working tirelessly behind the scenes to make it all possible.
9 Essential Tips for Operating System Optimization and Security
- Update your operating system regularly to ensure maximum security and performance.
- Make sure you have adequate antivirus protection installed on your system for maximum security.
- Avoid downloading software from unknown sources as it can contain malicious code or viruses that could damage your system.
- Backup important data regularly to avoid data loss in case of a crash or malware attack.
- Keep the number of applications installed on your system to a minimum to prevent any potential conflicts between programs and slow down the performance of your computer.
- Use disk defragmenter tools periodically to improve the speed and efficiency of hard disk accesses by reorganizing fragmented data files into contiguous blocks on the disk surface for better performance and reliability of the operating system .
- Monitor resources usage (CPU, RAM, Disk, etc.) closely so you can identify any bottlenecks in time and take necessary actions before they become critical problems that might affect overall system performance negatively .
- Be aware of potential hardware compatibility issues when installing new components such as graphic cards, sound cards or other peripherals that may not be compatible with certain versions of an operating systems .
- Always read instructions carefully before installing an OS or application software as mistakes during installation process may lead to serious problems later on .
Enhance Security and Performance: Regularly Update Your Operating System
In today’s interconnected digital landscape, where cyber threats lurk around every corner, ensuring the security and optimal performance of your devices is of paramount importance. One simple yet effective tip to achieve this is to regularly update your operating system (OS). By keeping your OS up-to-date, you can bolster your device’s security defenses and enjoy improved performance. In this article, we will explore the significance of updating your operating system and the benefits it brings.
Security is a primary concern for any digital user. Operating system updates often include crucial security patches that address vulnerabilities discovered by developers or reported by users. These vulnerabilities can potentially be exploited by malicious actors to gain unauthorized access to your device or data. By promptly installing OS updates, you stay one step ahead of potential threats, as these updates patch known vulnerabilities and fortify your device against emerging risks.
Moreover, regular OS updates contribute to maintaining optimal performance levels. Developers continually refine and optimize their operating systems to enhance efficiency and address any software bugs or glitches that may impact performance. These updates may include improvements in memory management, file system optimization, or even enhancements in power management algorithms. By staying updated, you ensure that your device runs smoothly and efficiently, delivering a seamless user experience.
Operating system updates also bring new features and functionalities that enhance usability and expand capabilities. These additions can range from improved user interfaces to new productivity tools or enhanced compatibility with the latest software applications. By updating your OS regularly, you ensure that you have access to the latest features offered by developers, allowing you to make the most out of your device’s potential.
Updating an operating system is typically a straightforward process. Most modern devices provide automatic update notifications or prompts when new updates are available. It is advisable to enable automatic updates if possible as it ensures a hassle-free experience where critical patches are installed promptly without requiring manual intervention.
However, it’s important to note that before initiating any updates, it is wise to back up your important data. While rare, there is always a slight possibility of unforeseen issues occurring during the update process. Having a recent backup ensures that even if something goes wrong, your data remains safe and recoverable.
In conclusion, updating your operating system regularly is an essential practice to ensure maximum security and performance for your devices. By staying up-to-date with the latest OS versions and patches, you fortify your device against potential threats while enjoying improved efficiency and new features. Embrace this simple yet impactful tip and make updating your operating system a regular part of your digital routine. Your device’s security and performance will thank you for it!
Make sure you have adequate antivirus protection installed on your system for maximum security.
Enhance Your System’s Security with Adequate Antivirus Protection
In today’s digital landscape, where cyber threats are constantly evolving, ensuring the security of your operating system is of utmost importance. One crucial step towards safeguarding your system is by having adequate antivirus protection installed. This small but significant measure can provide a strong defense against malicious software and potential cyberattacks. In this article, we will explore the importance of antivirus protection and how it can maximize the security of your operating system.
Antivirus software serves as a shield against various types of malware, including viruses, worms, Trojans, ransomware, and spyware. These malicious programs can infiltrate your system through infected files, email attachments, or compromised websites. Once inside your system, they can cause havoc by stealing sensitive information, corrupting files, or even taking control of your device.
By having antivirus protection installed on your operating system, you create an additional layer of defense that actively scans for and detects any suspicious activity or potential threats. Antivirus software employs sophisticated algorithms to identify and isolate malware before it can cause harm to your system or compromise your data.
Regularly updating your antivirus software is essential to ensure it remains effective against emerging threats. Developers continuously release updates that include new virus definitions and security patches to combat the latest malware strains. By keeping your antivirus software up to date, you stay one step ahead in the ongoing battle against cybercriminals.
Another key aspect of antivirus protection is real-time scanning. This feature actively monitors all incoming and outgoing data on your system in real-time. It scans files as they are accessed or downloaded to identify any potential threats immediately. Real-time scanning provides proactive protection by preventing malware from executing before it can cause damage.
In addition to real-time scanning, most modern antivirus solutions offer additional features such as web browsing protection and email scanning. These features help safeguard against malicious websites and infected email attachments that are common sources for malware distribution. By proactively blocking access to such threats, antivirus software acts as a gatekeeper, preventing potential vulnerabilities from being exploited.
While having antivirus protection is crucial, it is important to remember that it should not be your sole line of defense. Practicing safe browsing habits, regularly updating your operating system and applications, and exercising caution when downloading files from untrusted sources are equally important in maintaining a secure system.
In conclusion, ensuring you have adequate antivirus protection installed on your operating system is a vital step towards maximizing its security. Antivirus software acts as a shield against malware and provides real-time scanning to detect and neutralize threats promptly. By keeping your antivirus software up to date and practicing safe digital habits, you can significantly reduce the risk of falling victim to cyberattacks and protect your valuable data. Stay proactive and prioritize the security of your operating system for a safer digital experience.
Avoid downloading software from unknown sources as it can contain malicious code or viruses that could damage your system.
Protect Your System: Avoid Downloading Software from Unknown Sources
In today’s digital landscape, downloading software has become a routine part of our lives. From productivity tools to entertainment applications, the internet is filled with a plethora of software options. However, it is crucial to exercise caution and avoid downloading software from unknown sources. This simple tip can go a long way in safeguarding your system from potential harm.
When we refer to “unknown sources,” we mean websites or platforms that are not reputable or widely recognized. These sources may offer software downloads that appear tempting or even claim to be legitimate, but they often come with hidden risks. Such software might contain malicious code or viruses that can compromise the security and stability of your operating system.
One of the primary risks associated with downloading software from unknown sources is the potential for malware infection. Malware refers to malicious software designed to gain unauthorized access to your system, steal sensitive information, or cause damage. It can come in various forms such as viruses, worms, ransomware, or spyware.
By downloading software from trusted and reputable sources, you significantly reduce the chances of inadvertently installing malware on your system. Well-known platforms like official app stores (such as Google Play Store or Apple App Store) or verified websites maintained by renowned developers are generally safer options. These sources have strict security measures in place to ensure that their offered software is thoroughly vetted and free from harmful code.
When you download software from unknown sources, you expose yourself to several risks:
Security Breaches: Malicious software can compromise your personal data, including passwords, financial information, and private documents.
System Instability: Some unauthorized applications may not be properly tested or compatible with your operating system. This can lead to crashes, freezes, and other performance issues.
Loss of Control: Certain malicious programs can hijack your system resources and use them for illicit activities without your knowledge.
To protect your system, it is essential to follow these best practices:
Stick to Trusted Sources: Download software only from reputable sources such as official app stores or verified websites. Check user reviews and ratings before proceeding.
Enable Automatic Updates: Keep your operating system and installed applications up to date with the latest security patches and bug fixes. This helps protect against known vulnerabilities.
Use Antivirus Software: Install a reliable antivirus program that can detect and remove malware threats. Regularly update it to ensure optimal protection.
Exercise Caution with Email Attachments: Be wary of email attachments, especially from unknown senders, as they can contain malware. Avoid opening attachments unless you are confident in their legitimacy.
Educate Yourself: Stay informed about the latest cybersecurity threats and trends to make informed decisions regarding software downloads.
Remember, prevention is always better than dealing with the aftermath of a security breach or system damage caused by malicious software. By avoiding downloads from unknown sources, you take a proactive step towards maintaining the integrity of your operating system and protecting your digital assets.
Backup important data regularly to avoid data loss in case of a crash or malware attack.
The Importance of Regular Data Backup: Safeguarding Your Digital Assets
In today’s digital age, where our lives are intricately connected to technology, the safety and security of our data have become paramount. Whether it’s cherished memories captured in photos, important work documents, or personal information, losing valuable data can be devastating. That’s why it is crucial to regularly backup your important data to protect against unforeseen events such as system crashes or malware attacks.
An operating system crash or a malware attack can strike at any time, leaving you vulnerable to irretrievable data loss. Without a recent backup, recovering lost files can be a daunting and often impossible task. This is where the practice of regular data backup comes into play as your knight in shining armor.
By backing up your important data on a regular basis, you create an additional layer of protection for your digital assets. A backup essentially involves creating a duplicate copy of your files and storing them in a separate location or on an external storage device. This ensures that even if your primary storage becomes compromised or inaccessible, you have a secure copy that can be easily restored.
There are several methods available for backing up your data. One common approach is to use external storage devices such as external hard drives or USB flash drives. These devices offer ample space to store large amounts of data and can be easily connected to your computer for backup purposes. Additionally, cloud-based backup solutions have gained popularity in recent years due to their convenience and accessibility. Services like Google Drive, Dropbox, or iCloud allow you to store your files securely on remote servers and access them from anywhere with an internet connection.
When establishing a backup routine, it is essential to determine which files are critical and require regular backups. These may include personal documents, family photos, financial records, or any other irreplaceable information that holds value to you. By identifying these crucial files and including them in your regular backup process, you can ensure that they are protected against potential data loss.
Automating the backup process can also be beneficial. Many operating systems offer built-in backup tools or third-party software that allows you to schedule regular backups. This way, you can set it and forget it, knowing that your data is being backed up at predetermined intervals without requiring manual intervention.
Remember, a backup is only effective if it is up to date. It is recommended to perform backups regularly, depending on the frequency of changes and updates to your important files. For some, a weekly backup may suffice, while others may prefer a daily or even real-time backup solution.
In conclusion, regular data backup is an essential practice for safeguarding your digital assets. By taking the time to back up your important data on a consistent basis, you can protect yourself from the devastating consequences of system crashes or malware attacks. So don’t delay – start implementing a robust backup strategy today and enjoy peace of mind knowing that your valuable files are secure and easily recoverable in case of any unfortunate events.
Optimize Your Computer’s Performance: Minimize Installed Applications
In today’s digital age, our computers have become essential tools for work, communication, and entertainment. However, as we install numerous applications to meet our diverse needs, we may unintentionally burden our operating system (OS) and experience a decrease in performance. To ensure a smooth and efficient computing experience, it is crucial to keep the number of installed applications to a minimum.
Why is this important? When multiple applications are installed on your system, they consume valuable system resources such as memory (RAM), processing power (CPU), and storage space. This can lead to potential conflicts between programs that may cause crashes or slow down your computer’s overall performance.
By minimizing the number of installed applications, you can reduce the strain on your OS and allocate more resources to the essential software you regularly use. This allows your computer to run smoothly and respond quickly to your commands without unnecessary delays.
To achieve this, start by evaluating the applications you have installed on your computer. Ask yourself if each application is genuinely necessary for your daily tasks or if it serves a specific purpose that cannot be fulfilled by other software you already have. If you find any redundant or unused applications, consider uninstalling them to free up valuable resources.
It’s worth noting that some software may come with background processes or services that continue running even when you’re not actively using them. These processes consume system resources and can impact performance over time. Check your computer’s task manager or activity monitor to identify any resource-intensive background processes associated with installed applications. If they are not crucial for your workflow, disabling or uninstalling them can help improve performance.
Furthermore, keeping a tidy desktop by organizing files into folders can also contribute to better overall system performance. A cluttered desktop filled with shortcuts and files consumes additional system resources as the OS continuously renders icons and updates their status. By organizing files into folders within your user directory or other designated locations, you can reduce the strain on your OS and improve efficiency.
Remember, maintaining a lean and efficient system by minimizing installed applications is a proactive approach to ensure optimal performance. Regularly review your software needs and remove any applications that are no longer necessary. By doing so, you can enjoy a faster, more responsive computer experience while avoiding potential conflicts between programs.
Boost Your System’s Performance with Disk Defragmentation
Is your computer running slower than usual? Are you experiencing delays when accessing files or launching applications? If so, it might be time to consider using a disk defragmenter tool. Disk defragmentation is a process that reorganizes fragmented data files on your hard disk, resulting in improved speed and efficiency of disk accesses. In this article, we’ll explore the benefits of disk defragmentation and how it can enhance the performance and reliability of your operating system.
Over time, as you create, modify, and delete files on your computer, the data becomes scattered across different areas of the hard disk. This fragmentation occurs because the operating system allocates space for new files wherever available, leading to fragmented file storage. When you access fragmented files, the read/write heads of your hard disk have to move around more frequently to retrieve all the scattered pieces. This constant movement slows down your system’s performance.
By using a disk defragmenter tool, you can rearrange these fragmented files and store them in contiguous blocks on the disk surface. This consolidation eliminates the need for excessive head movement during file access, resulting in faster read/write speeds and reduced loading times for applications. The improved efficiency allows your operating system to access files more quickly and deliver a smoother overall user experience.
In addition to speed improvements, disk defragmentation also enhances the reliability of your operating system. When data is fragmented across multiple locations on the hard disk, there is an increased risk of file corruption or loss due to errors during read or write operations. By defragmenting your disks regularly, you minimize these risks as files are stored in a more organized manner.
Most modern operating systems come with built-in disk defragmenter tools that allow you to schedule automated defragmentation processes at regular intervals. These tools analyze your hard drive’s fragmentation levels and determine which files need to be rearranged for optimal performance. By setting up a regular defragmentation schedule, you can ensure that your system remains optimized and running smoothly.
It’s important to note that solid-state drives (SSDs) do not require defragmentation. Unlike traditional hard disk drives (HDDs), SSDs use flash memory to store data, and their performance is not affected by file fragmentation. In fact, defragmenting an SSD can actually decrease its lifespan due to the limited number of write cycles each flash memory cell can endure. Therefore, it’s best to avoid defragmenting SSDs and focus on optimizing their performance through other means, such as firmware updates or TRIM commands.
In conclusion, disk defragmentation is a simple yet effective way to improve the speed and efficiency of your operating system. By reorganizing fragmented files into contiguous blocks on your hard disk, you can enjoy faster access times, reduced loading delays, and a more reliable computing experience. So don’t let file fragmentation slow you down – unleash the full potential of your system by regularly using a disk defragmenter tool.
Optimize Your System Performance: Monitor Resources Usage
In the fast-paced digital world we live in, it’s crucial to ensure that our operating systems run smoothly and efficiently. One effective way to achieve this is by closely monitoring resource usage, such as CPU, RAM, disk space, and more. By keeping a vigilant eye on these metrics, you can identify potential bottlenecks before they escalate into critical problems that hamper overall system performance.
The central processing unit (CPU) acts as the brain of your computer, executing instructions and performing calculations. Monitoring CPU usage allows you to keep track of how much processing power is being utilized at any given time. High CPU usage can indicate resource-intensive tasks or poorly optimized software that may slow down your system. By identifying these bottlenecks early on, you can take necessary actions such as closing unnecessary applications or optimizing resource allocation to maintain optimal performance.
Random access memory (RAM) plays a vital role in storing data that the CPU needs to access quickly. Monitoring RAM usage helps you understand how efficiently your system utilizes available memory. When RAM usage approaches its maximum capacity, it can lead to sluggish performance or even crashes. By closely monitoring RAM usage, you can identify memory leaks or resource-hungry applications and take appropriate steps like closing unused programs or upgrading your system’s memory capacity.
Disk space is another critical resource that requires careful monitoring. As files accumulate over time, disk space can become limited and impact overall system performance. Insufficient disk space may hinder the operating system’s ability to perform routine tasks like caching data or creating temporary files. Regularly checking disk space usage allows you to identify bloated folders or unnecessary files that can be safely deleted to free up storage and enhance system responsiveness.
In addition to CPU, RAM, and disk space monitoring, it’s essential to keep an eye on other resources like network bandwidth and GPU utilization if applicable. Network bandwidth issues can affect internet connectivity and slow down data transfer rates. GPU utilization is particularly relevant for tasks that require graphics processing power, such as gaming or video editing. Monitoring these resources helps you pinpoint potential bottlenecks and take corrective measures to optimize performance.
By closely monitoring resource usage, you gain valuable insights into the health and efficiency of your operating system. Regularly checking these metrics allows you to address any emerging issues promptly, preventing them from escalating into critical problems that negatively impact overall system performance. Whether it’s closing unnecessary applications, optimizing resource allocation, or upgrading hardware components, taking necessary actions in a timely manner ensures a smooth and productive computing experience.
Remember, a well-optimized operating system leads to improved productivity, faster response times, and an overall smoother user experience. So don’t overlook the importance of monitoring resource usage – it’s the key to maintaining peak performance and maximizing the potential of your digital systems.
Be aware of potential hardware compatibility issues when installing new components such as graphic cards, sound cards or other peripherals that may not be compatible with certain versions of an operating systems .
Navigating Hardware Compatibility Issues When Installing New Components
When it comes to upgrading or enhancing our computer systems, adding new components such as graphic cards, sound cards, or other peripherals can significantly improve performance and functionality. However, it is crucial to be aware of potential hardware compatibility issues that may arise when installing these new components, especially with specific versions of an operating system.
Operating systems act as the bridge between software applications and the underlying hardware. They rely on drivers and software interfaces to communicate effectively with different hardware components. While modern operating systems strive to provide broad compatibility, there can still be instances where certain versions may not support specific hardware configurations.
One common scenario is when installing a new graphic card. Graphics cards are essential for gaming, video editing, graphic design work, and other visually demanding tasks. However, some high-end graphics cards may require the latest drivers or specific software features that are only supported by newer versions of an operating system. In such cases, attempting to install the latest graphics card on an older operating system version could lead to compatibility issues and prevent the card from functioning optimally.
Similarly, sound cards or other peripherals may also encounter compatibility challenges. These devices often rely on specific drivers or firmware updates that are designed for particular operating system versions. Installing a sound card without ensuring its compatibility with your existing OS version could result in audio distortion or complete loss of functionality.
To avoid these compatibility pitfalls, it is essential to research and verify hardware compatibility before making any purchases. Check the manufacturer’s website for information on supported operating systems and recommended driver versions for each component you plan to install. This will help ensure smooth integration and optimal performance between your hardware and operating system.
If you encounter compatibility issues after installing a new component, there are a few steps you can take to resolve them. First, check if there are updated drivers or firmware available from the manufacturer’s website specifically designed for your operating system version. Installing these updates may address any compatibility problems and restore full functionality.
If no updated drivers are available, you may need to consider upgrading your operating system to a version that supports your new hardware. However, before proceeding with an OS upgrade, ensure that your computer meets the system requirements for the new version and backup all important data to avoid any potential data loss during the transition.
In conclusion, being aware of potential hardware compatibility issues when installing new components is crucial for a smooth and successful upgrade process. Researching compatibility, checking for updated drivers or firmware, and considering operating system upgrades if necessary can help you avoid headaches and ensure that your new hardware functions optimally within your existing system setup. By taking these precautions, you can enjoy the benefits of enhanced performance without any unexpected compatibility roadblocks.
Always read instructions carefully before installing an OS or application software as mistakes during installation process may lead to serious problems later on .
The Importance of Reading Instructions Before Installing an Operating System or Application Software
In today’s fast-paced digital world, it’s easy to get caught up in the excitement of installing a new operating system (OS) or application software. However, it is crucial to take a step back and carefully read the instructions before proceeding with the installation process. Ignoring this essential step can lead to serious problems down the line.
Installation instructions are provided for a reason. They guide users through the installation process, ensuring that everything is set up correctly and smoothly. By reading and following these instructions, you can avoid common pitfalls and prevent potential issues from arising.
One of the primary reasons for reading instructions is to understand the system requirements. Different operating systems and software applications have specific hardware and software prerequisites. These requirements may include minimum processor speed, amount of RAM, available disk space, or even specific versions of other software components. Failing to meet these requirements can result in poor performance, instability, or even complete failure of the installed system or application.
Instructions also provide valuable guidance on how to configure settings during installation. This includes options related to language preferences, network settings, security configurations, and more. By carefully reviewing these options, you ensure that your system is set up according to your needs and preferences right from the start.
Moreover, installation instructions often highlight any potential risks or known issues associated with the OS or application software. This information allows you to make informed decisions about whether to proceed with the installation or seek alternative solutions if compatibility problems are anticipated.
Additionally, reading instructions helps users understand any additional steps required after installation. Some software may require activation codes or license agreements that need attention before full functionality is unlocked. By being aware of these post-installation requirements in advance, you can ensure a smooth transition from installation to usage without any unexpected interruptions.
Lastly, mistakes made during the installation process can have long-lasting consequences on your system’s stability and security. Rushing through the installation or skipping important steps can lead to corrupted files, software conflicts, or even malware infections. Taking the time to read and understand the instructions reduces the risk of encountering such issues and helps maintain a secure and reliable computing environment.
In conclusion, always remember to read instructions carefully before installing an operating system or application software. By doing so, you equip yourself with the necessary knowledge to ensure a successful installation process without any unwanted surprises later on. Take the extra few minutes to familiarize yourself with the requirements, configurations, and potential risks associated with the software you are installing. Your diligence will pay off in terms of system stability, performance, and overall user experience.