Unveiling NetworkMiner for Linux: Enhancing Network Analysis on Open-Source Platforms
Exploring NetworkMiner for Linux
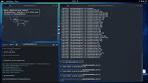
NetworkMiner is a popular network forensic analysis tool that has been widely used by cybersecurity professionals and network administrators. While traditionally available for Windows operating systems, the demand for a Linux version has been growing steadily. The good news is that NetworkMiner for Linux is now available, bringing its powerful features to the Linux community.
Features of NetworkMiner for Linux:
- Packet Sniffing: NetworkMiner allows users to capture and analyse packets in real-time, providing valuable insights into network traffic.
- File Extraction: The tool can extract files transferred over the network, helping investigators identify potential threats or sensitive data leaks.
- Host Detection: NetworkMiner can detect and profile hosts on the network, giving users visibility into connected devices.
- Keyword Search: Users can search for specific keywords within captured packets, making it easier to locate relevant information.
- User-Friendly Interface: NetworkMiner features an intuitive interface that simplifies the process of network analysis, even for beginners.
How to Install NetworkMiner on Linux:
To install NetworkMiner on a Linux system, follow these steps:
- Download the NetworkMiner installation package from the official website.
- Extract the downloaded package to a directory of your choice.
- Open a terminal window and navigate to the extracted directory.
- Run the installation script by executing the following command: ./install.sh
- Follow the on-screen instructions to complete the installation process.
Once installed, you can launch NetworkMiner from the application menu or by running it from the terminal. Start exploring its features and unleash its full potential in analysing network traffic and detecting security threats.
In conclusion, NetworkMiner for Linux is a valuable addition to any cybersecurity toolkit, offering powerful capabilities for network analysis and forensic investigations. Whether you are a cybersecurity professional or a network enthusiast, NetworkMiner provides an essential set of tools to enhance your understanding of network activity and security posture.
8 Essential Tips for Effectively Using NetworkMiner on Linux Systems
- Install NetworkMiner on a Linux system using Wine or PlayOnLinux for compatibility.
- Use NetworkMiner to capture and analyse network traffic for security monitoring purposes.
- Customise the settings in NetworkMiner to filter specific protocols or traffic types of interest.
- Export extracted files from NetworkMiner for further analysis using other tools.
- Regularly update NetworkMiner to ensure you have the latest features and security patches.
- Explore the various tabs in NetworkMiner, such as ‘Hosts’, ‘Sessions’, and ‘Files’ for detailed insights.
- Refer to online resources and guides to learn advanced techniques for using NetworkMiner effectively.
- Join forums or communities related to network forensics to share experiences and gain insights into using NetworkMiner.
Install NetworkMiner on a Linux system using Wine or PlayOnLinux for compatibility.
To enhance compatibility and expand the usability of NetworkMiner on a Linux system, users can opt to install the application using Wine or PlayOnLinux. By leveraging these compatibility layers, which allow Windows applications to run on Linux, users can seamlessly utilise NetworkMiner’s features and functionalities without encountering compatibility issues. This approach enables Linux users to harness the power of NetworkMiner while enjoying a smooth and efficient user experience, bridging the gap between Windows-based tools and the Linux environment for enhanced network forensic analysis capabilities.
Use NetworkMiner to capture and analyse network traffic for security monitoring purposes.
Utilise NetworkMiner on your Linux system to capture and analyse network traffic for enhanced security monitoring. By leveraging the capabilities of NetworkMiner, you can gain valuable insights into network activity, identify potential security threats, and monitor data transfers in real-time. This proactive approach to security monitoring empowers users to detect anomalies, investigate suspicious behaviour, and strengthen the overall security posture of their networks.
Customise the settings in NetworkMiner to filter specific protocols or traffic types of interest.
In NetworkMiner for Linux, a valuable tip is to customise the settings to filter specific protocols or traffic types of interest. By adjusting the settings, users can focus their analysis on particular protocols or types of network traffic, allowing for more targeted and efficient investigation. This feature enables users to hone in on relevant data, making it easier to identify potential threats, investigate anomalies, and extract valuable insights from the network traffic being analysed. Customising settings in NetworkMiner empowers users to tailor their analysis to suit their specific needs and objectives, enhancing the overall effectiveness of their network forensic analysis efforts.
Export extracted files from NetworkMiner for further analysis using other tools.
To enhance the analysis capabilities of NetworkMiner for Linux, users can export extracted files from the tool for further examination using other specialised tools. By exporting these files, users can leverage the strengths of different analysis tools to gain deeper insights into potential security threats, data leaks, or anomalous network activity. This process allows for a more comprehensive and detailed investigation, enabling cybersecurity professionals and network administrators to make informed decisions and take appropriate actions to secure their networks effectively.
Regularly update NetworkMiner to ensure you have the latest features and security patches.
It is essential to regularly update NetworkMiner on your Linux system to ensure that you are benefiting from the latest features and security patches. By keeping your NetworkMiner installation up-to-date, you can access new functionalities, improvements, and bug fixes that enhance the tool’s performance and usability. Additionally, staying current with updates helps protect your network analysis activities against potential vulnerabilities, ensuring a secure and efficient experience when using NetworkMiner for forensic analysis and network monitoring on Linux.
Explore the various tabs in NetworkMiner, such as ‘Hosts’, ‘Sessions’, and ‘Files’ for detailed insights.
To maximise your network analysis capabilities with NetworkMiner for Linux, be sure to explore the diverse tabs available within the application, including ‘Hosts’, ‘Sessions’, and ‘Files’. By delving into these tabs, users can gain in-depth insights into network activity, host profiles, active sessions, and extracted files. This exploration of different tabs not only enhances your understanding of network traffic but also enables you to uncover valuable information for forensic analysis and security monitoring.
Refer to online resources and guides to learn advanced techniques for using NetworkMiner effectively.
To maximise your proficiency in utilising NetworkMiner on Linux, it is advisable to refer to online resources and guides that delve into advanced techniques. These valuable sources can offer insights into leveraging the full potential of NetworkMiner, enabling you to enhance your network analysis skills and uncover more sophisticated functionalities within the tool. By exploring these resources, you can deepen your understanding of NetworkMiner and elevate your ability to effectively utilise its features for comprehensive network forensic analysis.
Join forums or communities related to network forensics to share experiences and gain insights into using NetworkMiner.
To maximise your experience with NetworkMiner for Linux, consider joining forums or communities dedicated to network forensics. By engaging with like-minded individuals in these platforms, you can share your experiences, exchange tips and tricks, and gain valuable insights into using NetworkMiner effectively. Networking with experts and enthusiasts in the field can broaden your understanding of network forensics and enhance your proficiency in leveraging NetworkMiner’s features for comprehensive network analysis and security investigations.