Enhancing Security: Choosing the Best Linux Distro for Enhanced Security Measures
The Best Linux Distribution for Security
When it comes to choosing a Linux distribution with a strong focus on security, there are several options available that cater to users who prioritise privacy, data protection, and system integrity. Let’s explore some of the best Linux distros known for their robust security features:
Tails
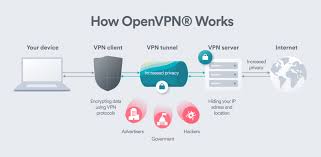
Tails is a privacy-focused Linux distribution that aims to preserve your anonymity and protect your data. It routes all internet traffic through the Tor network by default, ensuring that your online activities remain private and secure. Tails also comes with built-in encryption tools and secure communication apps.
Qubes OS
Qubes OS is a security-oriented operating system that compartmentalises applications into isolated virtual machines called “qubes.” This approach enhances security by preventing one compromised application from affecting the entire system. Qubes OS is designed with a strong focus on isolation and sandboxing.
Whonix
Whonix is a privacy-focused Linux distribution that runs inside virtual machines to provide an extra layer of security and anonymity. It routes all internet traffic through the Tor network and ensures that all connections are encrypted. Whonix is ideal for users who require high levels of privacy and security.
Fedora Security Lab
Fedora Security Lab is a Fedora spin dedicated to providing tools for penetration testing, forensics analysis, and secure development. It includes a wide range of security tools pre-installed, making it an excellent choice for security professionals and enthusiasts looking to test and enhance their systems’ defences.
Debian Privacy Tools
Debian offers a range of privacy tools in its repositories that can be installed on any Debian-based system to enhance security and privacy. These tools include encryption software, secure communication apps, and anonymity services, allowing users to customise their Debian installation according to their specific security needs.
Choosing the best Linux distribution for security ultimately depends on your specific requirements and comfort level with different security measures. Whether you prioritise anonymity, data encryption, or secure development practices, there is a Linux distro tailored to meet your security needs.
Top 6 FAQs on Choosing the Best Linux Distribution for Security and Privacy
- Which Linux distribution is considered the most secure for privacy and data protection?
- Are there any Linux distros that focus specifically on isolation and sandboxing for enhanced security?
- What are the key features of Tails, a popular privacy-focused Linux distribution?
- How does Qubes OS differ from other Linux distributions in terms of security?
- What tools are included in Fedora Security Lab for penetration testing and secure development?
- Can Debian Privacy Tools be installed on any Debian-based system to enhance security and privacy?
Which Linux distribution is considered the most secure for privacy and data protection?
When it comes to selecting a Linux distribution renowned for its emphasis on privacy and data protection, Tails often stands out as a popular choice among security-conscious users. Tails is specifically designed to safeguard user anonymity and privacy by routing all internet traffic through the Tor network by default. This ensures that online activities remain confidential and secure. With built-in encryption tools and secure communication applications, Tails offers a comprehensive solution for those seeking a highly secure operating system that prioritises privacy and data protection.
Are there any Linux distros that focus specifically on isolation and sandboxing for enhanced security?
When it comes to enhancing security through isolation and sandboxing, there are Linux distributions that specifically focus on these aspects to provide users with a heightened level of protection. Distributions like Qubes OS are designed with a strong emphasis on compartmentalising applications into isolated virtual machines, known as “qubes,” to prevent the spread of potential threats. By isolating each application within its own secure environment, these Linux distros ensure that even if one component is compromised, the rest of the system remains unaffected. Such dedicated focus on isolation and sandboxing makes these Linux distributions ideal choices for users seeking enhanced security measures in their computing environment.
What are the key features of Tails, a popular privacy-focused Linux distribution?
Tails, a well-known privacy-focused Linux distribution, is revered for its key features that prioritise user anonymity and data protection. One of its standout features is the automatic routing of all internet traffic through the Tor network, ensuring that users’ online activities remain private and secure. Tails also comes equipped with built-in encryption tools and secure communication applications to safeguard sensitive information. Additionally, Tails operates as a live operating system, meaning it runs entirely from a USB drive or DVD without leaving any trace on the host computer, further enhancing privacy and security measures. These features make Tails an excellent choice for individuals seeking a high level of anonymity and security while using a Linux distribution.
How does Qubes OS differ from other Linux distributions in terms of security?
Qubes OS stands out from other Linux distributions in terms of security due to its unique approach to system isolation. Unlike traditional distributions that run applications in a shared environment, Qubes OS utilises virtualisation technology to compartmentalise applications into separate, secure “qubes.” Each qube operates independently, reducing the risk of a security breach spreading across the system. This innovative design ensures that even if one qube is compromised, the integrity of other qubes remains intact. By implementing a strict isolation model and prioritising security through compartmentalisation, Qubes OS provides users with a highly secure computing environment that minimises the impact of potential threats on the overall system.
What tools are included in Fedora Security Lab for penetration testing and secure development?
The Fedora Security Lab, a specialised spin of the Fedora distribution, comes equipped with a comprehensive suite of tools tailored for penetration testing and secure development. Some of the key tools included in Fedora Security Lab for penetration testing are Metasploit, Nmap, Wireshark, John the Ripper, and Burp Suite. These tools assist security professionals in identifying vulnerabilities and assessing the security posture of systems. For secure development, Fedora Security Lab offers tools like Git, GDB debugger, Valgrind memory analysis tool, and various programming languages with their respective development environments. These tools empower developers to write secure code and conduct thorough testing to ensure robustness against potential threats.
Can Debian Privacy Tools be installed on any Debian-based system to enhance security and privacy?
Debian Privacy Tools offer a valuable array of security-enhancing features that can be installed on any Debian-based system to bolster security and privacy measures. Whether you are using Debian itself or a derivative distribution like Ubuntu or Linux Mint, the flexibility of these tools allows users to customise their system according to their specific security needs. By leveraging encryption software, secure communication applications, and anonymity services provided by Debian Privacy Tools, users can significantly enhance the protection of their data and online activities, making it a versatile choice for those seeking to fortify their system’s security posture.