Enhancing System Security and Compliance with Log Management Software
The Importance of Log Management Software
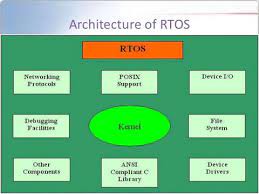
Log management software plays a crucial role in the effective monitoring and analysis of logs generated by various systems and applications. Logs are records of events that occur within a system, providing valuable insights into its operation, performance, and security.
Here are some key reasons why log management software is essential:
Security Monitoring
Logs contain information about user activities, system changes, and potential security threats. Log management software enables real-time monitoring of logs to detect suspicious activities, security breaches, or anomalies that may indicate a cyber attack.
Compliance Requirements
Many industries have regulatory compliance requirements that mandate the collection and retention of logs for auditing purposes. Log management software helps organisations meet these compliance standards by centralising log storage, ensuring data integrity, and facilitating log analysis.
Troubleshooting and Debugging
When issues arise within a system or application, logs can provide valuable diagnostic information to identify the root cause of problems. Log management software simplifies the process of troubleshooting by enabling log aggregation, search capabilities, and correlation of events across multiple sources.
Performance Monitoring
Monitoring system logs can help identify performance bottlenecks, resource utilisation trends, and areas for optimisation. Log management software offers features such as log visualisation, alerting mechanisms, and historical data analysis to track system performance over time.
Centralised Log Storage
By centralising logs from various sources into a single repository, log management software provides a unified view of system activities and events. This centralised approach simplifies log retention policies, improves searchability, and enhances overall visibility into the IT environment.
In conclusion, effective log management is essential for maintaining the security, compliance, performance, and reliability of IT systems. Investing in robust log management software can streamline log analysis processes, enhance operational efficiency, and strengthen overall cybersecurity posture.
Understanding Log Management Software: Key FAQs and Benefits
- What is log management software and what does it do?
- How does log management software help with security monitoring?
- What are the key features to look for in log management software?
- How can log management software assist with compliance requirements?
- What benefits does log management software offer for troubleshooting and debugging?
- How does log management software aid in performance monitoring?
- Why is centralised log storage important, and how does log management software facilitate this?
What is log management software and what does it do?
Log management software is a crucial tool for organisations to collect, store, and analyse log data generated by various systems and applications. It serves as a centralised platform for managing logs, providing insights into system activities, security events, performance metrics, and more. Log management software plays a key role in enhancing cybersecurity by enabling real-time monitoring for suspicious activities and potential threats. Additionally, it helps with troubleshooting issues, meeting compliance requirements, and improving overall system performance through effective log analysis and monitoring. In essence, log management software acts as a vital component in maintaining the integrity, security, and efficiency of IT infrastructures.
How does log management software help with security monitoring?
Log management software plays a vital role in security monitoring by providing real-time visibility into system activities and events. By collecting and analysing logs from various sources, such as servers, applications, and network devices, log management software can detect unusual patterns, anomalies, and potential security threats. Through advanced correlation algorithms and alerting mechanisms, it helps security teams identify suspicious activities, investigate security incidents promptly, and respond to threats effectively. Additionally, log management software enables organisations to maintain audit trails, monitor user access, and ensure compliance with security policies and regulations. Overall, log management software is a powerful tool for enhancing cybersecurity posture and proactively safeguarding against cyber attacks.
What are the key features to look for in log management software?
When considering log management software, it is essential to look for key features that can enhance the effectiveness of log analysis and monitoring. Some crucial features to consider include robust log collection capabilities to gather logs from various sources, scalable storage options to accommodate large volumes of data, advanced search and filtering functionalities for efficient log analysis, real-time alerting mechanisms to notify users of critical events, compliance reporting tools to meet regulatory requirements, and user-friendly dashboards for visualising log data. Additionally, features such as log retention policies, role-based access control, integration with existing systems, and automated log parsing can further streamline the log management process and improve overall operational efficiency. By prioritising these key features in log management software selection, organisations can effectively manage logs, enhance security monitoring practices, and troubleshoot issues more efficiently.
How can log management software assist with compliance requirements?
Log management software plays a vital role in assisting organisations with compliance requirements by facilitating the collection, storage, and analysis of logs to meet regulatory standards. By centralising log data from various systems and applications, log management software ensures that organisations can easily demonstrate compliance with industry regulations and data protection laws. Additionally, log management software offers features such as log retention policies, audit trails, and reporting capabilities that enable organisations to track and monitor log data effectively, helping them adhere to compliance requirements and maintain data integrity.
What benefits does log management software offer for troubleshooting and debugging?
Log management software offers several benefits for troubleshooting and debugging processes. One key advantage is the ability to centralise logs from various sources, providing a unified view of system activities and events. This centralised approach simplifies the identification of issues by enabling quick access to all relevant log data. Additionally, log management software facilitates log aggregation, search capabilities, and correlation of events across different sources, making it easier to pinpoint the root cause of problems. By streamlining the troubleshooting process and enhancing visibility into system performance, log management software plays a crucial role in improving operational efficiency and reducing downtime.
How does log management software aid in performance monitoring?
Log management software plays a crucial role in performance monitoring by providing a comprehensive view of system activities and events. By aggregating logs from various sources into a centralised repository, log management software enables IT teams to track performance metrics, identify trends, and pinpoint areas for optimisation. With features such as log visualisation, alerting mechanisms, and historical data analysis, organisations can gain valuable insights into resource utilisation, application performance, and system health. This proactive approach to performance monitoring allows for the timely detection of bottlenecks, anomalies, and inefficiencies, ultimately leading to improved system performance and reliability.
Why is centralised log storage important, and how does log management software facilitate this?
Centralised log storage is crucial in log management for several reasons. By consolidating logs from various sources into a single repository, organisations can streamline log analysis, improve searchability, and enhance overall visibility into system activities. Centralised storage simplifies the process of monitoring and managing logs, making it easier to track events, troubleshoot issues, and identify potential security threats. Log management software plays a key role in facilitating centralised log storage by providing features such as log aggregation, indexing, and search capabilities. These tools enable users to collect logs from disparate sources, store them in a central location, and efficiently retrieve and analyse log data for monitoring, compliance, troubleshooting, and performance analysis purposes.