Advancing the Future: Linux Technology Advancements Unleashed
Linux Technology Advancements: Empowering the Future of Computing
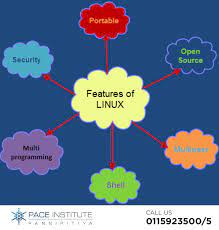
Linux, the open-source operating system, has been at the forefront of technological advancements for decades. With its robust architecture, flexibility, and strong community support, Linux has continuously evolved to meet the ever-changing demands of the computing world. In this article, we will explore some of the key advancements in Linux technology that have shaped the landscape of modern computing.
Containerization: Revolutionizing Software Deployment
One of the most significant advancements in Linux technology is containerization. Containers provide a lightweight and isolated environment for running applications, enabling efficient resource utilization and simplified deployment. Docker, a popular containerization platform built on Linux, has revolutionized software development by streamlining application packaging and delivery.
Cloud Computing: Powering Scalability and Flexibility
Linux plays a vital role in the cloud computing revolution. The scalability and flexibility offered by Linux-based cloud platforms have transformed how businesses operate. Leading cloud providers such as Amazon Web Services (AWS) and Google Cloud Platform heavily rely on Linux to deliver their services reliably and securely.
Internet of Things (IoT): Connecting a Smart World
The rise of IoT devices has been made possible by Linux technology. With its small footprint and adaptability, Linux is an ideal choice for powering smart devices that make up the IoT ecosystem. From smart home appliances to industrial sensors, Linux-based operating systems enable seamless connectivity and data exchange in our increasingly interconnected world.
High-Performance Computing (HPC): Pushing Boundaries
Linux is widely used in high-performance computing environments where immense computational power is required. Supercomputers around the world run on Linux due to its stability, scalability, and ability to efficiently manage complex tasks across multiple nodes. This advancement in Linux technology has accelerated scientific research breakthroughs across various fields.
Security Enhancements: Protecting Digital Assets
As cyber threats continue to evolve, so does Linux’s security capabilities. The Linux community actively develops and maintains robust security features, ensuring that Linux-based systems remain resilient against vulnerabilities. Technologies like SELinux (Security-Enhanced Linux) provide mandatory access controls, while projects like AppArmor offer application-level security policies, safeguarding critical data and infrastructure.
Desktop Environments: User-Friendly Interfaces
Linux desktop environments have come a long way in terms of user-friendliness and visual appeal. Projects such as GNOME, KDE Plasma, and Cinnamon provide intuitive interfaces with customizable features, making Linux more accessible to a wider audience. These advancements have contributed to the growing popularity of Linux as a viable alternative to proprietary operating systems.
Open-Source Collaboration: Driving Innovation
The collaborative nature of the open-source community has been instrumental in advancing Linux technology. Developers from around the world contribute their expertise to improve existing features and create new innovations. This collective effort ensures that Linux remains at the forefront of technological advancements, constantly pushing boundaries and adapting to emerging trends.
In conclusion, Linux technology continues to shape the future of computing with its remarkable advancements. From containerization to cloud computing, IoT to high-performance computing, Linux has become an integral part of various domains. With its strong emphasis on security, user-friendly interfaces, and open-source collaboration, Linux is poised to empower the next generation of technological breakthroughs while maintaining its core principles of freedom and accessibility for all.
Exploring Linux Technology Advancements: 5 Frequently Asked Questions
- How Linux has changed the world?
- What technologies use Linux?
- What made Linux successful?
- Is Linux the future of computing?
- What is the trend in Linux in 2023?
How Linux has changed the world?
Linux, the open-source operating system, has had a profound impact on the world of technology and beyond. Here are some ways in which Linux has changed the world:
- Open-Source Movement: Linux embodies the spirit of open-source software, where code is freely available for anyone to view, modify, and distribute. This philosophy has revolutionized the software industry by promoting collaboration, transparency, and innovation.
- Accessibility: Linux has made computing accessible to a wider audience. Its availability as a free operating system has empowered individuals and organizations with limited resources to access powerful software without licensing costs.
- Stability and Reliability: Linux is known for its stability and reliability. It powers critical infrastructure worldwide, from servers to supercomputers, ensuring uninterrupted operation for businesses, research institutions, and governments.
- Customizability: Linux offers unparalleled customizability. Users can tailor their Linux distributions to suit their specific needs by selecting different components and configurations. This flexibility enables users to create efficient systems that cater to their unique requirements.
- Security: Linux’s security track record is impressive due to its strong focus on security measures and prompt vulnerability patching by the community. The transparent nature of open-source development allows security experts worldwide to scrutinize the code continually.
- Innovation: Linux has been a catalyst for innovation across various industries. Its open nature encourages experimentation and enables developers to build upon existing technologies freely. Many cutting-edge technologies such as containerization (Docker), cloud computing (OpenStack), and IoT (Raspberry Pi) have been made possible or significantly influenced by Linux.
- Cost Savings: The adoption of Linux often results in significant cost savings for businesses and individuals alike. By using free software alternatives instead of proprietary solutions, organizations can reduce licensing fees while maintaining high-quality software.
- Community Collaboration: The vibrant Linux community is a driving force behind its success. Developers, enthusiasts, and users collaborate globally through forums, mailing lists, and conferences to share knowledge, address issues, and contribute to the improvement of Linux.
- Education: Linux has played a crucial role in education. Its availability and customizability have made it a popular choice for educational institutions worldwide. Linux-based distributions provide students with hands-on experience in programming, system administration, and other technical skills.
- Empowering Developing Nations: Linux has been instrumental in bridging the digital divide by providing affordable technology solutions to developing nations. Its low hardware requirements and free software ecosystem make it an ideal choice for regions with limited resources.
In summary, Linux has changed the world by promoting open-source collaboration, making computing accessible, ensuring stability and reliability, fostering innovation, enhancing security measures, enabling cost savings, building strong communities, revolutionizing education, and empowering developing nations. Its impact on technology and society continues to grow as it remains at the forefront of technological advancements and societal change.
What technologies use Linux?
Linux is a versatile operating system that is used in a wide range of technologies and industries. Here are some notable examples:
- Servers: Linux is widely used as the operating system for servers due to its stability, security, and scalability. Many web servers, database servers, cloud servers, and enterprise servers run on Linux.
- Cloud Computing: Leading cloud platforms such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure heavily rely on Linux to provide their services. Linux powers the infrastructure that enables virtual machines, containers, and serverless computing in the cloud.
- Mobile Devices: Android, the most popular mobile operating system globally, is built on a modified version of the Linux kernel. Linux provides the foundation for millions of smartphones, tablets, and other mobile devices.
- Internet of Things (IoT): Linux-based operating systems are widely used in IoT devices due to their small footprint and adaptability. From smart home devices to industrial sensors and wearables, Linux powers the connectivity and intelligence behind IoT ecosystems.
- Supercomputers: Many of the world’s fastest supercomputers run on Linux-based operating systems. The high-performance computing (HPC) community relies on Linux for its stability, scalability, and ability to efficiently manage complex computational tasks.
- Networking Equipment: Linux is extensively used in networking infrastructure such as routers, switches, firewalls, and network appliances. It provides a reliable foundation for managing network traffic and ensuring secure communication.
- Automotive Systems: Linux has found its way into modern vehicles as an operating system for infotainment systems, navigation systems, advanced driver-assistance systems (ADAS), and autonomous driving platforms.
- Embedded Systems: Due to its flexibility and customizability, Linux is often chosen as the operating system for embedded systems like set-top boxes, digital signage displays, point-of-sale terminals, industrial automation controllers, and more.
- Desktops and Laptops: While Linux has a smaller market share compared to proprietary operating systems, it is gaining popularity as a user-friendly and customizable alternative. Many individuals and organizations use Linux distributions as their primary desktop or laptop operating system.
- Scientific Research: Linux is widely used in scientific research environments for its ability to handle complex computations, simulations, and data analysis tasks efficiently.
These are just a few examples of the many technologies that utilize Linux. Its open-source nature, robustness, and adaptability have made it a preferred choice for various applications across different industries.
What made Linux successful?
Several factors have contributed to the success of Linux:
- Open-Source Philosophy: Linux’s success can be attributed to its open-source nature. The availability of source code allows developers worldwide to contribute, modify, and improve the operating system. This collaborative approach fosters innovation, accelerates development, and ensures that Linux remains adaptable to emerging technologies.
- Stability and Reliability: Linux is renowned for its stability and reliability. It is known to power critical systems in industries such as finance, healthcare, and telecommunications. Its robust architecture and efficient memory management make it a preferred choice for mission-critical applications where downtime is not an option.
- Flexibility and Customization: Linux offers unparalleled flexibility and customization options. Users have the freedom to tailor their operating system according to their specific needs by selecting different distributions (distros) or configuring various desktop environments. This adaptability has attracted a wide range of users, from casual home users to advanced developers.
- Wide Hardware Support: Linux supports a vast array of hardware architectures, making it compatible with a wide range of devices – from servers and desktop computers to embedded systems and IoT devices. This versatility has helped Linux gain popularity across diverse industries.
- Security Focus: Security has always been a priority in the development of Linux. The open-source nature allows for continuous scrutiny by a global community of developers who actively identify vulnerabilities and release timely security patches. Additionally, the permission-based access control mechanisms employed by Linux enhance system security.
- Cost Efficiency: Being open-source software, Linux is freely available for anyone to use, modify, or distribute without licensing fees or restrictions. This cost advantage has made it an attractive choice for individuals, businesses, educational institutions, governments, and organizations with limited budgets.
- Community Support: The vibrant Linux community plays a crucial role in its success. The community provides support through forums, mailing lists, chat channels, and documentation resources that help users troubleshoot issues, share knowledge, and collaborate on projects. The strong community support fosters a sense of belonging and encourages the growth and adoption of Linux.
- Compatibility with Standards: Linux adheres to open standards, ensuring compatibility with various protocols, file formats, and software frameworks. This compatibility allows seamless integration with existing systems and promotes interoperability across different platforms.
In summary, Linux’s success can be attributed to its open-source philosophy, stability, flexibility, wide hardware support, security focus, cost efficiency, community support, and compatibility with standards. These factors have collectively contributed to its widespread adoption and positioned Linux as a leading operating system in the technology landscape.
Is Linux the future of computing?
Linux has undoubtedly established itself as a significant player in the world of computing. Its open-source nature, flexibility, and robustness have made it a preferred choice for many individuals, businesses, and organizations. However, whether Linux is the future of computing is a subjective question that depends on various factors and perspectives.
One key aspect that makes Linux a strong contender for the future of computing is its adaptability. Linux can be found in almost every domain, from smartphones to servers, IoT devices to supercomputers. Its versatility allows it to power a wide range of applications and systems, making it well-suited for the evolving needs of technology.
Another factor contributing to Linux’s potential as the future of computing is its strong community support. The passionate developer community continuously contributes to improving Linux’s features and addressing vulnerabilities promptly. This collaborative effort ensures that Linux remains at the cutting edge of technological advancements.
Additionally, Linux’s emphasis on security and privacy aligns with the growing concerns around data protection and cyber threats. As more individuals and organizations prioritize security in their computing choices, Linux’s robust security measures make it an attractive option.
However, it is important to note that other operating systems also have their strengths and are widely used across different sectors. Proprietary operating systems like Windows and macOS continue to dominate certain markets due to their compatibility with specific software or ease of use for certain applications.
Furthermore, user familiarity plays a significant role in determining the future of computing. Many users are accustomed to particular operating systems or software ecosystems, which can influence their preference when choosing a computing platform.
In conclusion, while Linux has made significant strides in shaping the present and future of computing with its open-source philosophy, versatility, security features, and community support, it is difficult to definitively state whether it will completely dominate the landscape. The future of computing will likely involve a diverse mix of operating systems catering to different needs and preferences while continuing to evolve alongside emerging technologies.
What is the trend in Linux in 2023?
The trend in Linux in 2023 is likely to be focused on cloud computing, containerization, and automation. As businesses become increasingly reliant on digital infrastructure, the need for secure, efficient, and reliable operating systems is growing. Linux will continue to be the preferred platform for hosting applications and services due to its open source nature and its ability to integrate with a wide range of technologies. Additionally, advances in artificial intelligence (AI) will likely lead to more automation within Linux-based systems.