Exploring the Diversity of Open Source Linux Distros
The Power of Open Source Linux Distros
Linux distributions, commonly known as distros, have revolutionised the world of operating systems by offering a vast array of choices to users. Among these, open-source Linux distros stand out for their transparency, flexibility, and community-driven development.
What Makes Open Source Linux Distros Unique?
Open source Linux distros are built on the principles of collaboration and shared knowledge. The source code of these distributions is freely available for anyone to view, modify, and distribute. This transparency not only fosters innovation but also ensures that users have full control over their computing experience.
Benefits of Using Open Source Linux Distros
- Customisation: With open source Linux distros, users have the freedom to customise every aspect of their operating system to suit their needs and preferences.
- Security: The open nature of these distributions allows for quicker identification and patching of security vulnerabilities, making them inherently more secure.
- Community Support: Open source Linux distros are backed by a passionate community of developers and users who provide support, share knowledge, and contribute to the continuous improvement of the distro.
- Cost-Effective: Most open source Linux distros are available free of charge, making them a cost-effective choice for individuals and organisations looking for reliable computing solutions.
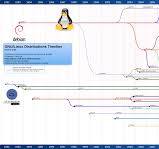
Popular Open Source Linux Distros
Some well-known open source Linux distros include:
In Conclusion
Open source Linux distros offer a powerful alternative to proprietary operating systems by providing users with freedom, security, and community support. Whether you are a beginner or an experienced user, exploring open source Linux distros can open up new possibilities in your computing journey.
Understanding Open Source Linux Distros: Answers to Common Questions
- What is an open source Linux distro?
- Why should I choose an open source Linux distro over a proprietary operating system?
- Are open source Linux distros free to use?
- How do I select the right open source Linux distro for my needs?
- Can I run software designed for other operating systems on an open source Linux distro?
- Is technical support available for users of open source Linux distros?
- How often are updates and new releases made available for open source Linux distros?
- What are some popular applications or tools available on open source Linux distros?
What is an open source Linux distro?
An open source Linux distro, short for distribution, is a version of the Linux operating system that is developed and distributed under an open-source license. This means that the source code of the distro is freely available for anyone to view, modify, and distribute. Open source Linux distros embody principles of transparency, collaboration, and community-driven development. Users have the freedom to customise the distro to suit their needs, benefit from enhanced security through community scrutiny, and access a wealth of support and resources from the vibrant open-source community.
Why should I choose an open source Linux distro over a proprietary operating system?
When considering whether to choose an open source Linux distro over a proprietary operating system, the key factors to keep in mind are freedom, security, and community support. Open source Linux distros offer users unparalleled freedom to customise their operating system according to their needs and preferences, without being locked into a specific vendor’s ecosystem. Additionally, the transparent nature of open source software allows for quicker identification and resolution of security vulnerabilities, making these distros inherently more secure than proprietary alternatives. Furthermore, the vibrant community surrounding open source Linux distros provides users with a wealth of knowledge, support, and resources to enhance their computing experience. Ultimately, opting for an open source Linux distro empowers users with control, security, and a collaborative environment that fosters innovation and continuous improvement.
Are open source Linux distros free to use?
Open source Linux distros are indeed free to use, in both senses of the word. Not only are they available at no cost to users, but they also embody the principles of freedom and accessibility that define the open-source movement. Users can download, install, and modify these distributions without any financial barriers, making them an attractive choice for individuals and organisations seeking cost-effective and flexible computing solutions. The freedom to use open source Linux distros without restrictions highlights the inclusive nature of the open-source community and underscores the collaborative spirit that drives innovation in the world of operating systems.
How do I select the right open source Linux distro for my needs?
When choosing the right open source Linux distro for your needs, it is essential to consider several factors to ensure a seamless computing experience. Firstly, assess your level of expertise in using Linux as some distributions are more beginner-friendly while others cater to advanced users. Next, identify your specific requirements such as software compatibility, hardware support, and the availability of community support. Research different distros to understand their features, desktop environments, package management systems, and update mechanisms. Ultimately, selecting the right open source Linux distro involves aligning your preferences and technical requirements with the strengths and characteristics of the distribution to find the perfect match for your computing needs.
Can I run software designed for other operating systems on an open source Linux distro?
Running software designed for other operating systems on an open source Linux distro is possible through various compatibility layers and tools. While some applications may require additional configuration or virtualisation, many popular software packages can be run seamlessly on Linux using compatibility solutions such as Wine for Windows applications or CrossOver for Microsoft Office suite. Additionally, the open-source community continually develops and improves compatibility layers to enhance the user experience and broaden the range of software that can be used on Linux distributions, making it a versatile choice for users seeking flexibility in their computing environment.
Is technical support available for users of open source Linux distros?
One frequently asked question regarding open source Linux distros is whether technical support is available for users. The answer is yes, technical support is often readily accessible for users of open source Linux distributions. These distros typically have vibrant and active communities of developers, enthusiasts, and experienced users who are willing to provide assistance through forums, chat channels, and online documentation. Additionally, some commercial entities offer professional support services for open source Linux distros, ensuring that users have access to expert help when needed. The collaborative nature of open source software fosters a culture of mutual support and knowledge sharing, making it easier for users to troubleshoot issues and maximise the potential of their chosen distribution.
How often are updates and new releases made available for open source Linux distros?
Updates and new releases for open source Linux distros vary depending on the specific distribution. Generally, most open source Linux distros follow a regular release schedule, with updates and new versions being made available every few months to a year. However, some distributions offer rolling releases, where updates are continuous and users receive the latest features and security patches as soon as they are ready. It is essential for users to stay informed about the update policies of their chosen Linux distro to ensure they are receiving timely updates and staying current with the latest developments in the open-source community.
What are some popular applications or tools available on open source Linux distros?
Open source Linux distros offer a vast array of popular applications and tools that cater to a wide range of user needs. Some commonly used software available on these distributions include the LibreOffice suite for productivity tasks, GIMP for image editing, VLC Media Player for multimedia playback, Firefox and Chromium for web browsing, and Thunderbird for email management. Additionally, development tools such as Git, Python, and GCC are widely used by programmers on open source Linux distros for software development. These applications exemplify the diverse and robust ecosystem of software available on open source Linux distributions, empowering users with powerful tools to enhance their computing experience.